Secrets in pipelines
Use Kubernetes secrets in Codefresh
Once you have connected Codefresh to your secrets storage, you can use them in any pipeline or UI screen.
NOTE
This feature is for Enterprise accounts only.
Using secrets in pipelines
The syntax for using the secret is ${{secrets.NAME_IN_CODEFRESH.KEY}}.
NOTE
If you did not include the resource-name as a part of your secret store context creation, the syntax for using your secret differs slightly:
${{secrets.NAME_IN_CODEFRESH.RESOURCE-NAME@KEY}}codefresh.yaml
version: '1.0'
steps:
step:
type: freestyle
arguments:
image: alpine
commands:
- echo $SECRET- Use the secret directly in your YAML
codefresh.yaml
version: '1.0'
steps:
step:
type: freestyle
arguments:
image: alpine
environment:
- SECRET=${{secrets.test.key1}}
commands:
- echo $SECRETUsing secrets in the Codefresh UI
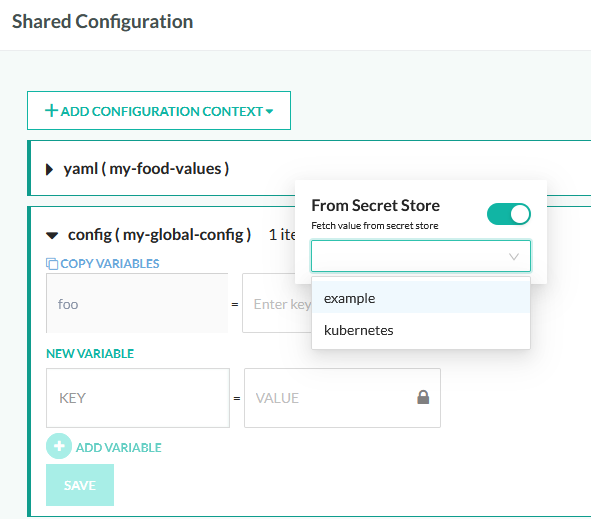
You can also use secrets in the GUI screens that support them. Currently you can use secrets in:
- Values in shared configuration
- Integration with cloud storage
Where secret integration is supported, click on the lock icon and enable the toggle button. You will get a list of your connected secrets:
If you have already specified the resource field during secret definition the just enter on the text field the name of the secret directly, i.e. my-secret-key.
If you didn’t include a resource name during secret creation then enter the full name in the field like my-secret-resource@my-secret-key.