Azure SSO via OIDC
Set up Azure SSO for OIDC
Set up SSO for Azure using OIDC. For a general overview on OIDC, see Setting up OIDC Federated SSO.
Set up OIDC SSO for Azure in Codefresh by:
- Registering the Codefresh application in Azure
- Configuring permissions for the Codefresh application in Azure
- Creating the Client secret in Azure
- Completing SSO configuration for Azure in Codefresh
- Configuring redirect URIs in Azure
Prerequisites
Make sure that your user in Azure who creates the application is assigned either of these roles:
Application Administrator
OR
Global Administrator
If the user who creates the Azure application is not assigned to either of these roles, you will be unable to sync teams from Azure to Codefresh.
Step 1: Register the Codefresh application in Azure
To setup Azure Active Directory for SSO, first register a new application in Azure.
- Log in to the Azure Portal, and from the sidebar, select Azure Active Directory.
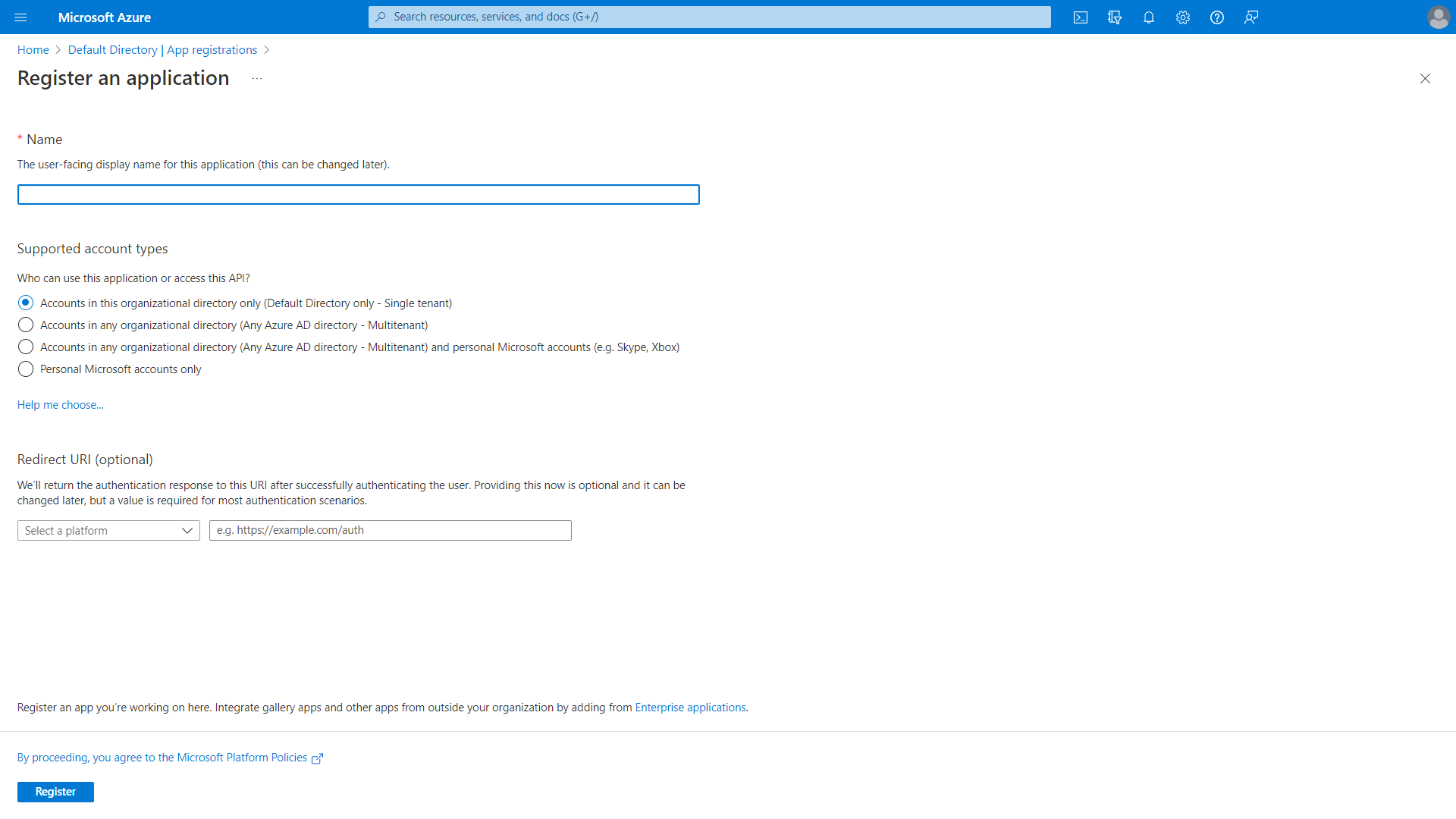
- From the sidebar, select App registrations, and then click + New registration.
- Enter a name for the application, for example,
Codefresh, and retain the default values for all other settings.
- To apply your changes, click Register. The application is created and registered in Azure AD.
- Continue with Step 2: Configure permissions for the application in Azure.
Step 2: Configure permissions for the application in Azure
Once the application has been created and registered, configure the required permissions.
- Click the name of the application to open Settings.
- Do the following:
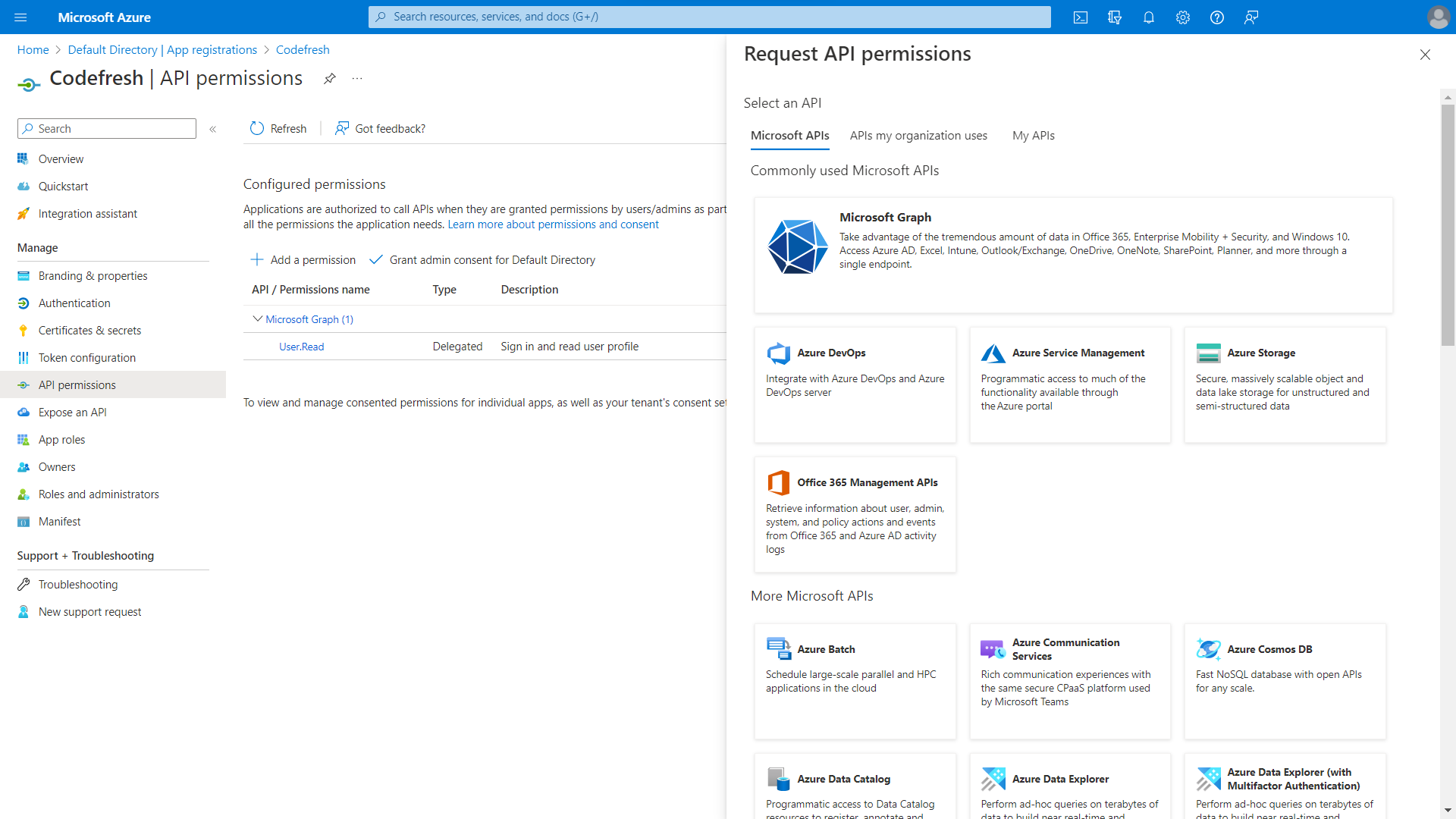
- Select API permissions, and then click + Add a permission.
- From Request API Permissions, select Microsoft APIs, and then select Microsoft Graph.
- Click Application permissions on the left.
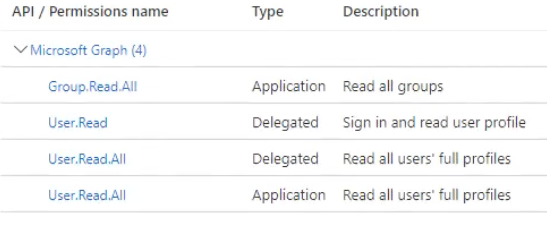
- Add
Group > Read.All - Add
User > Read.All
- Add
- Next add Delegated permissions on the right
- Add
User > Read.All
NOTE
TheUser.Read (Delegated)permission is added by default. - Add
- Click Add Permissions.
- Click Grant admin consent for Default Directory on the bar.
- Continue with Step 3: Create client secret in Azure.
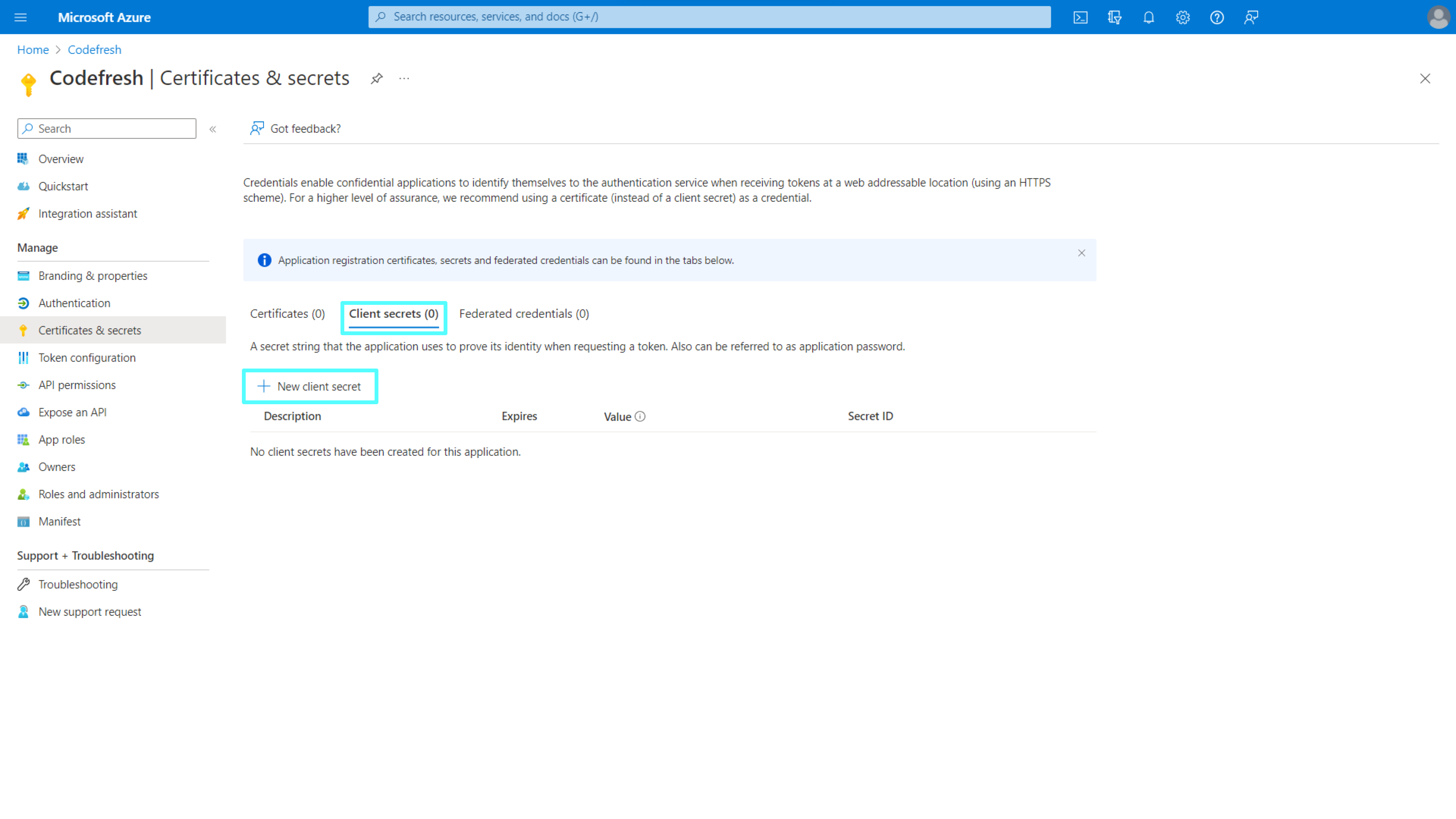
Step 3: Create client secret in Azure
Create a client secret for the application. You will need to provide it when you set up SSO for Azure in Codefresh.
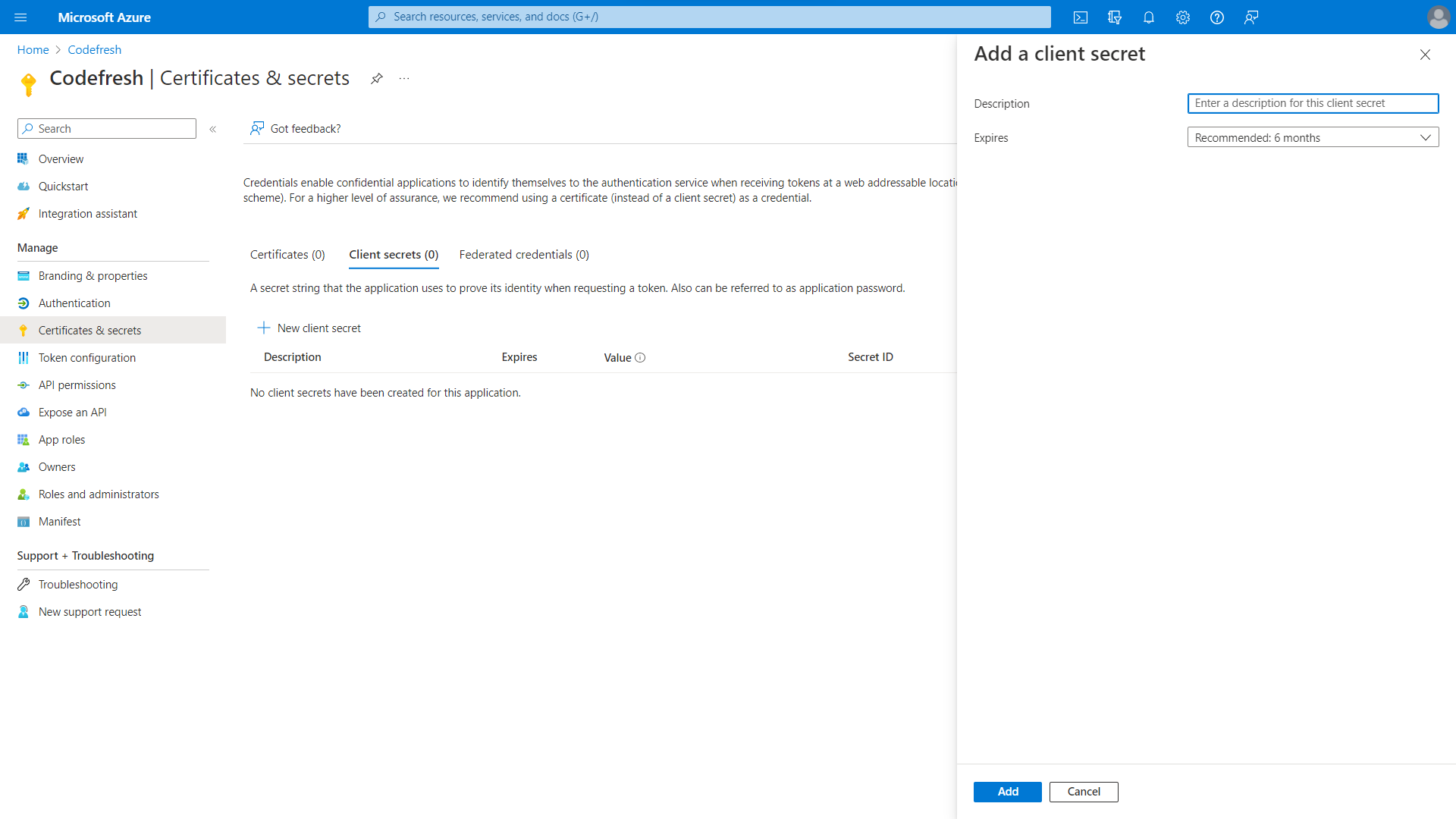
- From the sidebar, select Certificates & secrets, and then click + New client secret.
- Optional. Add a meaningful description for the client secret, and either retain the default expiry date or define a custom one.
TIP
Make a note of the expiry date in your calendar to renew the key before the expiry date and prevent service interruptions.
- Click Add.
Copy the secret key, as you will need to provide it on setting up Azure SSO in Codefresh. - Continue with Step 4: Configure SSO settings for Azure in Codefresh.
Step 4: Configure SSO settings for Azure in Codefresh
Configure SSO for Azure in the Codefresh UI.
Before you begin
- From Azure AD:
- Have your client secret handy
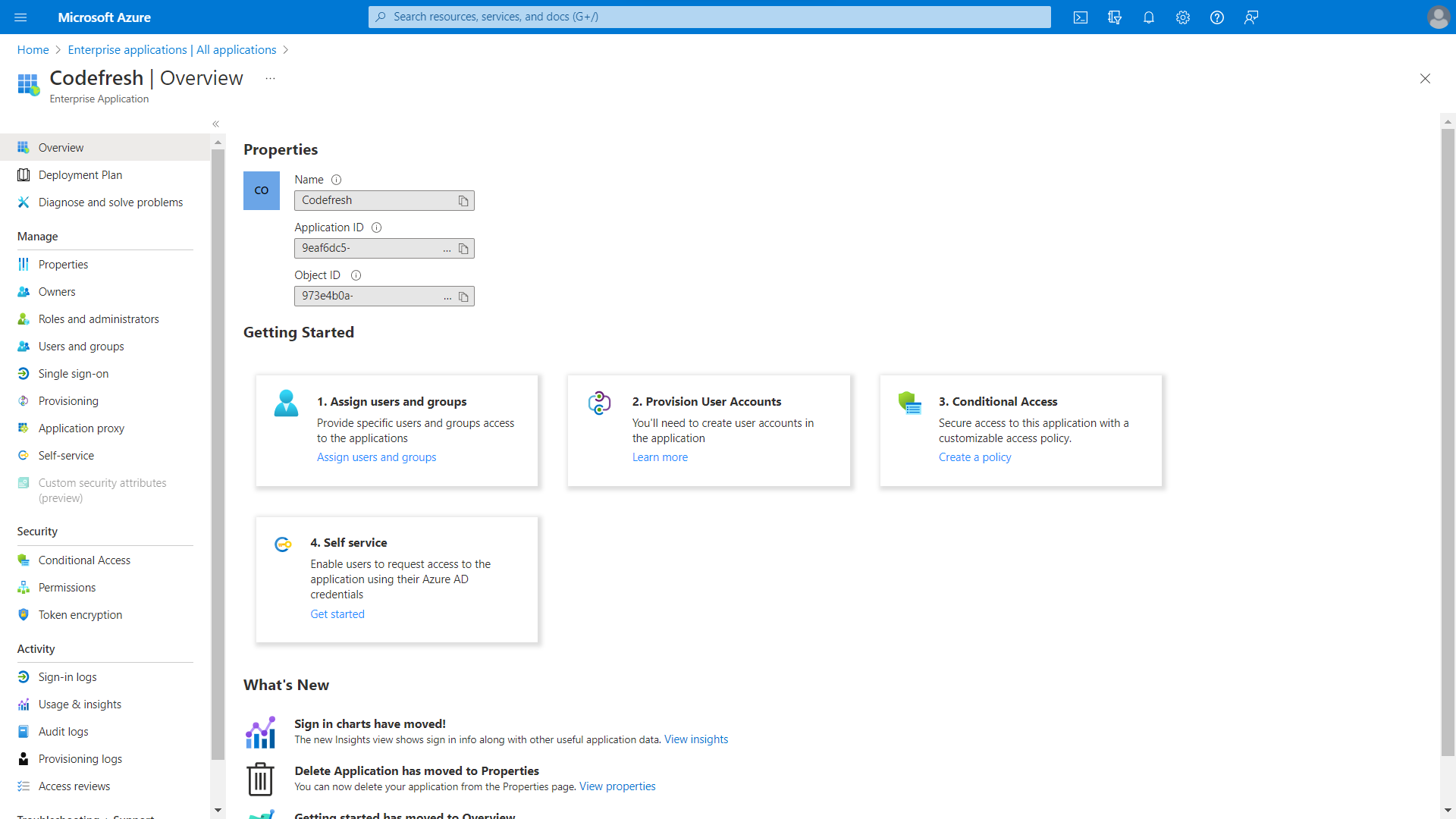
- Go to tAzure Active Directory > Enterprise Applications and select the app you created, and note down these Properties: Application ID and Object ID
How to
- In the Codefresh UI, from the toolbar, click the Settings icon.
- In the sidebar, from Access & Collaboration, select Single Sign-On.
- Click Add Single Sign-On, and select Azure, and click Next.
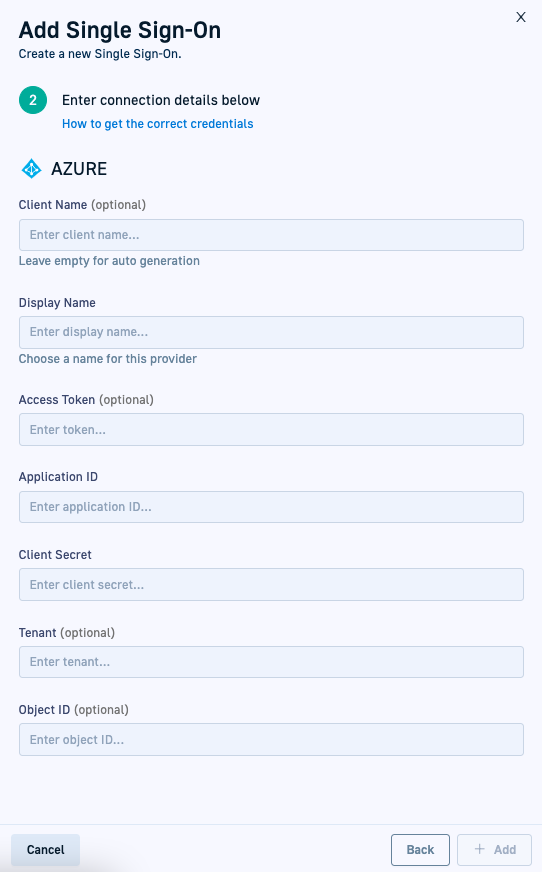
- Enter the following:
- Client Name: For auto-generation, leave empty. Codefresh generates the client name once you save the settings.
- Display Name: Meaningful name for the SSO provider. This is the name shown in Azure.
- Application ID: The Application ID from your Enterprise Application Properties in Azure AD.
- Client Secret: The key value you copied when you created the client secret in Azure.
- Tenant:
mycompany.onmicrosoft.comor the ID of0example1-0000-0aa0-a00a-1example0 - Object ID: The Object ID from your Enterprise Application Properties in Azure AD.
- Auto Sync users and teams to Codefresh: Select to automatically sync user accounts in Azure AD to your Codefresh account. Optionally, define the time interval, in hours, at which to sync, from 1 to 24. If you don’t specify an interval, the sync is every 12 hours.
- Click Save.
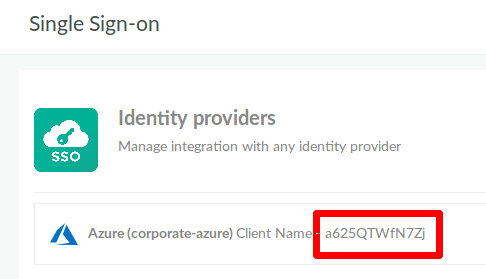
If you left the Client Name empty, Codefresh generates one (see example below). Codefresh uses this name to identify the SSO configuration.
You will need this value as the Reply URL setting in the Azure portal.
- Continue with Step 5: Configure redirect URIs in Azure.
Step 5: Configure redirect URIs in Azure
As the final step, add the Codefresh callback URL to the allowed reply URLs for the created application in Azure.
Before you begin
- Make sure you have the Client Name for the Azure SSO configuration from Codefresh
How to
- Go to Azure Active Directory > Apps registrations, and select the application you registered for SSO.
- From the sidebar, select Authentication.
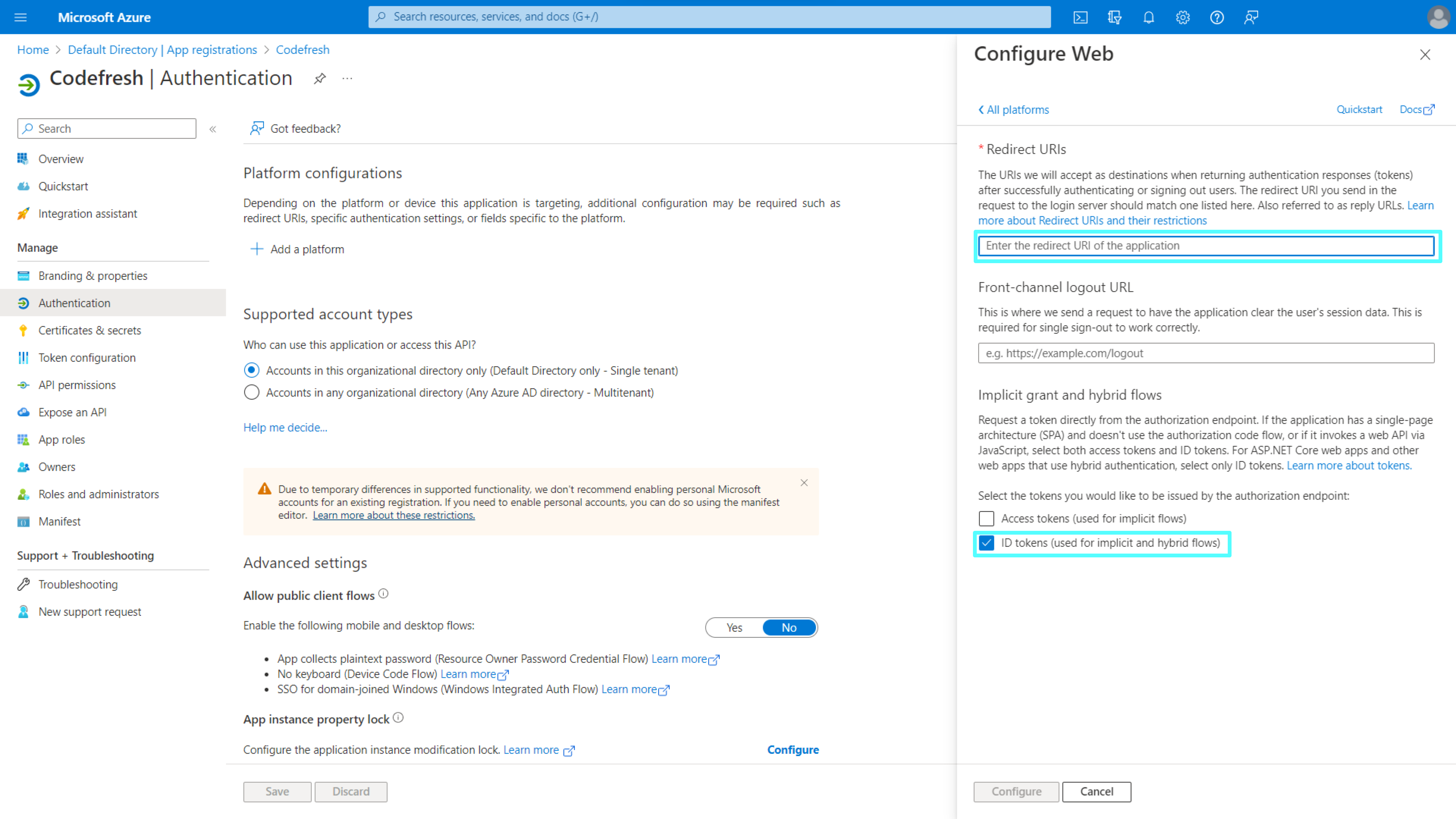
- Below Platform Configuration, click Add a platform and then select Web.
- In the Configure Web form, do the following:
- In the Redirect URIs field, enter the redirect URI in the format below:
https://g.codefresh.io/api/auth/<your_codefresh_sso_client_name>/callback
where:
<your_codefresh_sso_client_name>is the Client Name shown in the SSO configuration, either defined by you or created by Codefresh. - Select ID tokens.
- In the Redirect URIs field, enter the redirect URI in the format below:
Step 6: (Optional) Configure for Azure Initiated Login.
- Go to Azure Active Directory > Apps registrations, and select the application you registered for SSO.
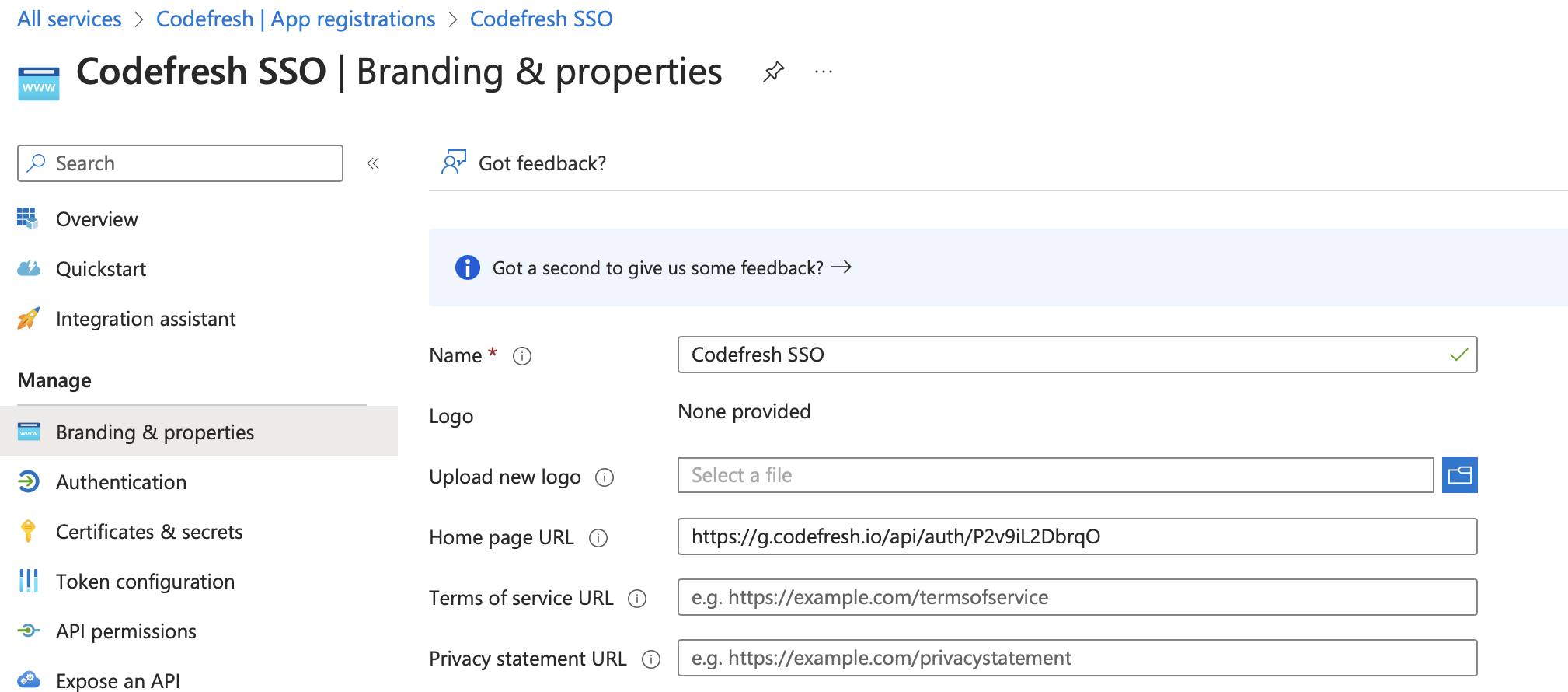
- From the sidebar, select Branding & properties
- In the Home page URL field, insert the following
https://g.codefresh.io/api/auth/<your_codefresh_sso_client_name>
- Go to Azure Active Directory > Enterprise Applications, and select the application you registered for SSO.
- Under Properties, toggle Visible to users to yes.
- Now the app can be added to a Collection for My Apps page for Azure Initiated Login.
You have now completed the SSO setup for Azure using OIDC.
Related articles
Federated Single Sign-On (SSO) overview
Common configuration for SSO providers