LDAP Single Sign-On (SSO)
To configure SSO for LDAP in Codefresh, you need to first create a user on your LDAP server who has permissions to search other users. Usually,
this user is an LDAP admin.
Make sure also that you know the scope of the search, that is, where users to search for are located in the LDAP hierarchy.
Step 1: Configure SSO settings for LDAP in Codefresh
- In the Codefresh UI, from the toolbar click the Settings icon.
- From the sidebar, select Single Sign-On.
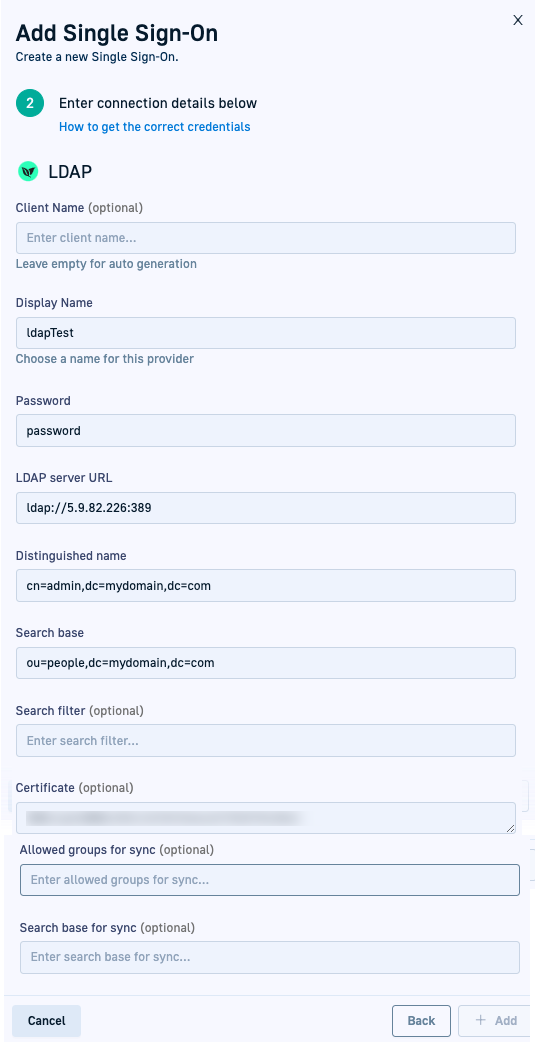
- Select + Add Single Sign-On, LDAP, and then Next.
- Enter the following:
- Client Name: For auto-generation, leave empty. Codefresh generates the client name once you save the settings.
- Display Name: Any meaningful name for this integration.
- Password: The password of the user defined in Distinguished name that will be used to search other users.
- LDAP Server URL: Codefresh supports both
ldapandldapsprotocols. Forldaps, you also need a certificate. - Distinguished name: The username to be used to search other users in LDAP notation (combination of
cn,ou,dc). - Search base: The search-user scope in LDAP notation.
- Search filter: The attribute by which to search for the user on the LDAP server. By default, set to
uid. For the Azure LDAP server, set this field tosAMAccountName. - Certificate:
- For
ldaps: The security certificate of the LDAP server. Paste the value directly on the field. Do not convert to base64 or any other encoding by hand. - For
ldap: Leave the field empty.
- For
- Allowed groups for sync:
- To sync only by specified groups, select the option, and define the groups for which to sync teams.
- To sync by all groups in the directory defined by Search base, leave the field empty.
- Search base for sync:
- To synchronize using a custom search base, define the search base.
- To find entries for synchronization within the scope defined by Search base, leave the field empty.
- Select + Add. LDAP users can now log in to Codefresh.
NOTE
Each user who logs in to Codefresh must:
- Have a defined email address on the LDAP server
- Use the same email address as defined on the LDAP server
- Use as login information, the LDAP email, password, and
cnvalue of username
Step 2: Synchronize teams with LDAP
Synchronize teams in Codefresh with LDAP using the Codefresh CLI.
TIP
Team synchronization is implemented based on the SSO options configured for LDAP in Codefresh.
-
Run the synchronize teams command:
codefresh synchronize teams <client_name> --client-type ldapwhere:
<client_name>is the Client Name that you either defined or is auto-generated by Codefresh in the LDAP SSO settings. For example,KK5XhWAx90rw.
Related articles
About Federated Single Sign-On (SSO)
Setting up OIDC Federated SSO
Setting up SAML2 Federated SSO