GitOps Amazon ECR integration
Integrate Amazon ECR with GitOps for image enrichment
Codefresh offers native support for interacting with Amazon ECR (Elastic Container Registry), enabling you to push, pull, and deploy container images seamlessly.
For general information on container registry integrations for GitOps, see Container registry GitOps integrations.
GitOps Amazon ECR integration options
You can set up the integration with Amazon ECR in one of two modes:
- IAM (Identity and Access Management) role (dynamic integration)
IAM roles provide temporary security credentials for applications and services to access AWS resources securely, that expire after a period of time. - Access key and secret (static integration)
Access keys consist of an access key ID and a secret access key, used to authenticate and authorize API requests to AWS services for a specific user. Unlike IAM roles, access keys are long-term credentials, without a default expiration date.
NOTE
Access Key integration requires Runtime version 0.1.27 or higher.
Both IAM and access key modes use AWS Identity and Access Management (IAM) to create the integration with Amazon ECR.
For detailed information, see How Amazon Elastic Container Registry Works with IAM and the AWS security blog.
Prerequisites
Permissions for IAM Role and Access Key integrations
The IAM Role/Access Key user must have one of the following permissions:
AmazonEC2ContainerRegistryReadOnlyfor read-only access to Amazon EC2 Container Registry repositories.AmazonEC2ContainerRegistryFullAccessfor administrative access to Amazon ECR resources.AmazonEC2ContainerRegistryPowerUserfor full access to Amazon EC2 Container Registry repositories, without permissions to delete repositories or make changes to policies.
If any of these permissions are not granted, images cannot be successfully reported from ECR.
IAM Role integration
IAM Role for ECR integration
Amazon ECR integration in Codefresh requires an Identity and Access Management (IAM) Role with permissions to the ECR registry. For details, see Create the ECR integration IAM role.
Other IAM roles
Once you have an ECR integration IAM Role, you can use a different IAM role if that Role can assume the ECR integration IAM Role.
To use an IAM Role assigned to the Service Account used by app-proxy for example, the Role must be explicitly configured with a trust relationship to assume the ECR integration IAM Role - even if the other IAM Role is the ECR integration IAM Role.
For example:
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::XXXXX:role/eksctl-awscluster-ServiceRole-XXXXXX" # IAM role for ECR integration
},
"Action": "sts:AssumeRole",
"Condition": {}
}
Access Key integration
You must generate an access key ID and the access secret for the IAM user, and download or copy them to a secure location.
NOTE
The steps that follow describe access key generation through the AWS Management Console. We assume that you have created the IAM user for whom to generate the access key. See Creating an IAM user in your AWS account.
- Sign in to the AWS Management Console, and go to the IAM dashboard.
- In the left pane, click Users, and select the IAM user for whom to generate an access key.
- Click the Security credentials tab.
- Below Access keys, click Create access key.
- From Access key best practices & alternatives, select Command Line Interface (CLI).
- Select I understand the above recommendation… and then click Next.
- Enter an optional description and then click Create access key.
- Click Download .csv file, or copy the Access key ID, and the Secret access key which is automatically generated to a secure location.
You will need to define them in the integration settings. - Click Done.
Amazon ECR-GitOps integration settings in Codefresh
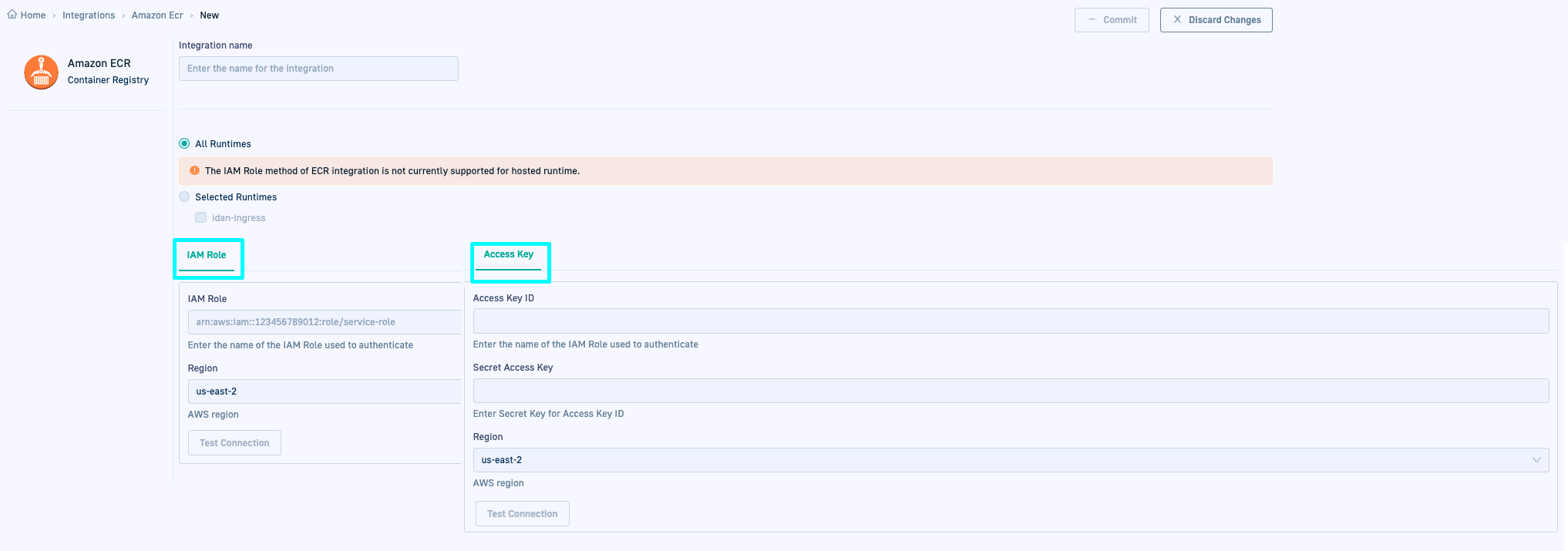
The table describes the arguments required for GitOps integrations with Amazon ECR in Codefresh.
| Setting | Description |
|---|---|
| Integration name | A friendly name for the integration. This is the name you will reference in the third-party CI platform/tool. |
| All Runtimes/Selected Runtimes | The runtimes in the account with which to share the integration resource. The integration resource is created in the Git repository with the shared configuration, within resources. The exact location depends on whether the integration is shared with all or specific runtimes:
|
| IAM Role settings | IAM Role integration is not supported for Hosted GitOps Runtimes.
|
| Access Key settings | Access Key integration is supported for both Hosted and Hybrid GitOps Runtimes.
|
| Test connection | Click to verify that you can connect to the specified instance before you commit changes. |
For how-to instructions, see Configure container registry integrations for GitOps in Codefresh and Edit/delete container registry integrations for GitOps in Codefresh.
Related articles
Shared Configuration Repository
Image enrichment with GitOps integrations
CI GitOps integrations
Issue-tracking GitOps integrations