Secret management has been one of the most challenging areas when it comes to application deployments. Especially in the era of containers and dynamic services that come and go all the time, secret storage and rotation is more important than ever.
Today we release our brand-new secret management integration that allows you to use Kubernetes secrets and configmaps straight into Codefresh pipelines in the easiest way possible.
First, you need to choose which secret you want to make available to Codefresh, via our secret storage integration.
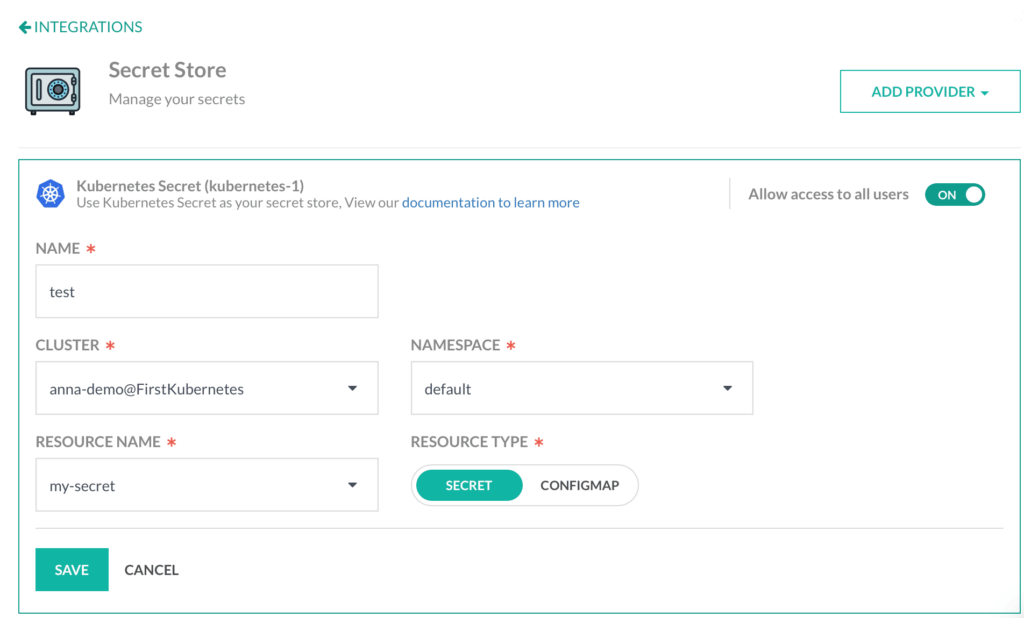
With the new integration, you can retrieve secrets from your existing clusters that are already connected to Codefresh via the standard Kubernetes integration methods.
To use a secret in a pipeline just mention it by name using the following syntax:
version: '1.0'
steps:
step:
type: freestyle
arguments:
image: alpine
environment:
- SECRET=${{secrets.test.key1}}
commands:
- echo $SECRET
That’s it!
You can now pass the secret to the pipeline and use it for performing integration tests, accessing a database, calling an external service, etc.
Using Kubernetes clusters for secret storage
Up until now, if you wanted to use secrets in Codefresh pipelines, as a customer you had to adopt one of the following approaches:
- Using a dedicated secret solution such as Hashicorp vault and loading secrets with the Codefresh Vault plugin
- Using the secret support in Codefresh shared configuration
Each approach has advantages and disadvantages. Using a dedicated secret solution is usually a strict requirement for security-sensitive organizations, but maintaining the secret solution requires a lot of effort and not all companies want to invest in such heavyweight solutions.
Using the shared configuration capabilities of Codefresh is an easy way to handle secrets, but places the storage backend on Codefresh itself, and not all organizations want to have secrets in the same place as their CI/CD solution.
Realizing that we needed an alternative solution between those two extremes, we understood that it is best to offer our customers the ability to use the native secret support of a Kubernetes cluster.
This approach has three major advantages:
- There is no extra maintenance burden, as secrets are stored in the cluster itself and thus operators reuse their existing Kubernetes knowledge
- Secret lifecycle can be managed independently outside of Codefresh
- Codefresh is accessing those secrets like any other Kubernetes client, splitting completely the duties of where secrets are stored and where they are used (in CI/CD pipelines)
It is also important to understand that because Codefresh is accessing a Kubernetes cluster via standard service accounts, it is very easy to isolate secrets between your CI/CD platform and other actors. You don’t have to trust Codefresh with secrets anymore if you prefer to restrict cluster access with specific roles and namespaces.
Creating Secret contexts with the Codefresh runner
Earlier this month we announced the Codefresh Runner, a way to run Codefresh pipelines in your own cluster. In this mode, the Web UI or Codefresh still runs in the cloud, but all builds are happening in the cluster of your choosing behind the company firewall.
As an alternative way to store secrets, we also offer the capability to use your own clusters (runtime environments) for secret storage in a much more friendly manner.
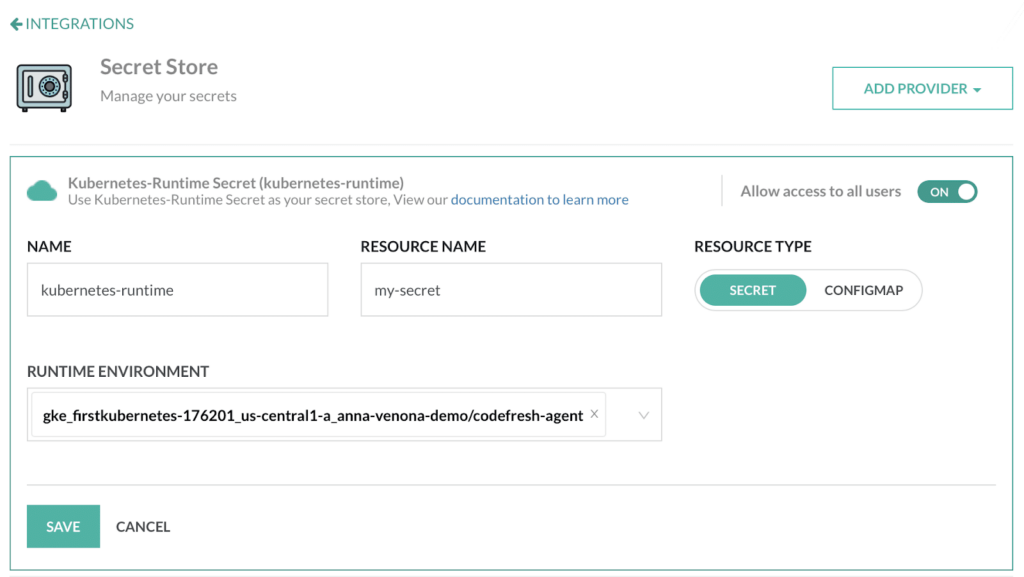
In this case, Codefresh does not even have access to the Kubernetes cluster itself, make this approach even more secure (the Codefresh runner only has outgoing network access to the Codefresh UI)
This means that you are free to store secrets:
- On Kubernetes clusters that you use for deployments
- On Kubernetes clusters that you use to run pipelines
- A mixture of both approaches
We believe that this amount of flexibility can help organizations to decide on their own how they want to manage their secrets instead of imposing them a specific way of storage.
The new secret storage feature also plays really well with our secret masking feature for protecting secrets from appearing in pipeline logs.
Secret Storage for Kubernetes clusters is rolled out to all Codefresh Enterprise accounts. If it is not enabled in your account yet, please contact us.
For more detailed information on how to use secrets from both the UI as well the Codefresh CLI, please visit the documentation page.
New to Codefresh? Create Your Free Account today!