Terraform is one of the pioneers of infrastructure as code (IaC). It provides a high-level configuration language that codifies APIs into declarative configuration files. This means that instead of manually configuring your own infrastructure or via a cloud vendor’s interface, you define and provide data center infrastructure using a code-based approach.
The main advantage of IaC with Terraform is its provider-agnostic nature. This means it can work with on-premise infrastructure and any cloud service provider, allowing you to manage a multi-cloud environment with a consistent set of tools and processes. It also integrates with version control systems, enabling you to track changes, roll back if needed, and work collaboratively with your team.
IaC with Terraform allows you to codify your infrastructure, reducing the risk of human error and promoting consistency and repeatability. It enables you to create, change, and improve infrastructure safely and efficiently, providing a streamlined way to manage your resources.
Core Concepts of Terraform
Configuration Files
Configuration files are the heart of Terraform’s operations. These files, written in HashiCorp Configuration Language (HCL), describe the infrastructure resources required for your application. They specify what resources to create and how to configure them.
The main benefit of using configuration files in Terraform is that they’re human-readable and machine-friendly. This means they’re easy to understand and maintain, and they can be shared and collaborated on within your team.
Moreover, configuration files allow you to define your infrastructure in a high-level syntax. This means you don’t need to worry about the underlying details, but instead focus on the higher-level structure of your resources.
Terraform Providers
Terraform Providers act as the bridge between Terraform and the various service APIs it interacts with. These providers offer a collection of resource types, each of which corresponds to a specific management feature of the given API.
Terraform providers let you manage a wide variety of services, from infrastructure resources like compute instances and storage, to critical configuration components such as DNS entries. Terraform has hundreds of providers for common services and platforms. You can find a large variety of providers in the Terraform registry.
Furthermore, since Terraform is provider-agnostic, it doesn’t matter which service you’re using; you’ll employ the same processes and workflows, ensuring consistency across your infrastructure.
State Management
Terraform maintains a state file that contains the current state of your managed infrastructure and configuration. This state is used by Terraform to map resources to your configuration, keep track of metadata, and improve performance for large infrastructures.
The state file plays a critical role in understanding how to create, modify, and delete resources. It also ensures that Terraform knows what real resources correspond to the resources defined in your configuration files.
Moreover, state files can be shared and locked, allowing multiple people to work with the same infrastructure safely. This promotes collaboration and ensures that your infrastructure remains consistent and up-to-date.
Plan and Apply Lifecycle
The Plan and Apply lifecycle is a fundamental process in Terraform:
- The “Plan” command is used to create an execution plan, showing what actions Terraform will take to achieve the desired state. It provides a preview of the changes, allowing you to validate and review them before applying.
- The “Apply” command is then used to apply the desired changes to reach the expected state. It executes the actions proposed in the execution plan.
This lifecycle ensures safe and predictable changes, allowing you to understand the impact of your actions before making them. This reduces the risk of unforeseen consequences and promotes a reliable and efficient infrastructure management process.
Modules
Modules in Terraform are self-contained packages of Terraform configurations that are managed as a group. They are used to create reusable components and organize your infrastructure code into logical segments.
Modules allow you to encapsulate a set of resources and make them reusable across multiple projects. This promotes code reuse, reduces duplication, and enhances the maintainability of your infrastructure code.
Moreover, modules can be shared and used by other teams, allowing you to standardize and enforce certain configurations across your organization.
Benefits of Terraform for IaC
Platform Agnostic
Terraform supports a wide array of service providers, allowing you to manage a diverse range of infrastructures. This feature makes Terraform a flexible and versatile tool for infrastructure management.
With Terraform, you can manage different infrastructures from a single place using the same language. This eliminates the need to learn and use different languages and tools for different platforms, saving time and effort. Moreover, it helps maintain consistency across different infrastructures and eases the process of scaling and transitioning between platforms.
Modularity and Reusability
Terraform promotes modularity and reusability, which are crucial elements in today’s fast-paced development environments. With Terraform, you can create modules, which are building blocks for multiple resources that are used together. These modules can be used across different projects, promoting reusability and reducing the time and effort needed to set up infrastructures.
Modules in Terraform not only increase efficiency but also improve the organization of code, making it easier to manage and maintain. This modular approach also ensures that infrastructures are set up in a standardized way across different projects, leading to more predictable and reliable systems.
Immutable Infrastructure
Terraform builds on the concept of immutable infrastructure, which is an approach where servers are never modified after they’re deployed. If something needs to be updated, fixed, or modified in any way, new servers are built from a common image, and old servers are discarded.
This approach brings a host of benefits, including reduced inconsistencies, faster deployment times, and easier troubleshooting. It also eliminates the problems associated with configuration drift, which occurs when production servers diverge from their original configuration.
Integrated with Major CI/CD Tools
Terraform’s integration with major Continuous Integration/Continuous Deployment (CI/CD) tools lets you automate the process of testing and deploying infrastructure changes, leading to faster and more reliable deployments.
Most CI/CD tools have built-in support for Terraform, making it easy to incorporate into your existing workflows. This seamless integration helps streamline operations and enhance productivity, allowing businesses to deliver better services to their customers.
Tutorial: Using Terraform on AWS
To get a better idea of how to implement IaC with Terraform, let’s see how the process works in AWS. Remember that Terraform supports all cloud providers and also on-premises infrastructure, so this is just one example of an environment you can automate with Terraform.
Step 1: Installing Terraform
To kick things off, we need to install Terraform on our system, which is a simple process. Terraform is available for download from the official HashiCorp website.
Download the appropriate package for your operating system and architecture. For example, in Ubuntu, run the following command: sudo apt-get install terraform.
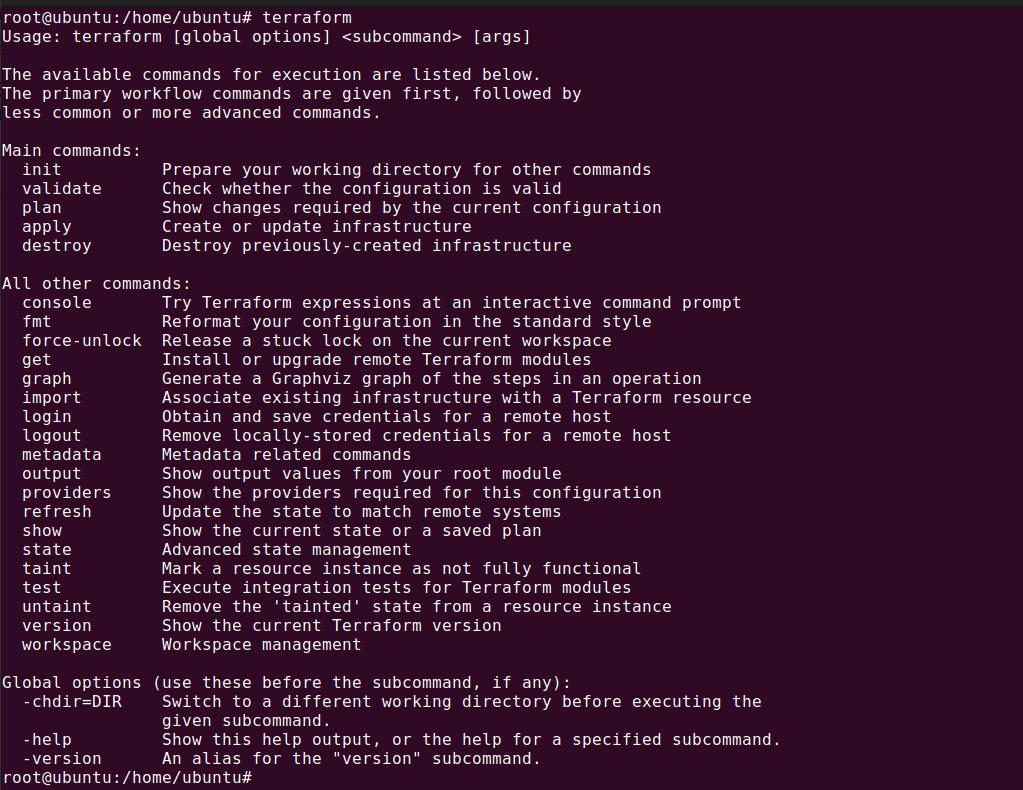
Once the installation is complete, you can verify it by opening a new terminal window and typing terraform. If the installation was successful, you should see a list of all the available Terraform commands.
Step 2: Setup AWS IAM Access
After installing Terraform, the next step is setting it up with AWS. This involves logging into your AWS account, setting up an IAM user, and setting your access keys.
In your AWS Console, navigate to the IAM service and create a new user. Ensure that Programmatic Access is enabled for this user, as this allows AWS services to be accessed via the API.
Finally, you’ll need to set your access keys. These keys allow Terraform to authenticate with AWS. In your AWS Console, navigate to My Security Credentials and create a new access key. Make sure to keep these keys secure, as they grant access to your AWS resources.
To manage credentials from your workstation, install the awscli utility. Once you have it installed, run this command to set up your credentials: aws configure. This is an easy way to gain access for the purpose of this tutorial, but you should consider other authentication options for production environments.

Step 3: Write Your First Terraform Configuration
Terraform configurations are written in HashiCorp Configuration Language (HCL). It’s a declarative language, which means you describe your desired state, and Terraform figures out how to achieve it.
To write your first Terraform configuration, create a new file in your Terraform directory with the extension .tf. This file will contain your configuration.
A basic Terraform configuration for AWS might look something like this:
provider "aws" {
region = "us-west-2"
}
resource "aws_instance" "example" {
ami = "ami-0b3b8df738695dd85"
instance_type = "t2.micro"
}Once you have the configuration in your directory, run terraform init again. The output should look like this:
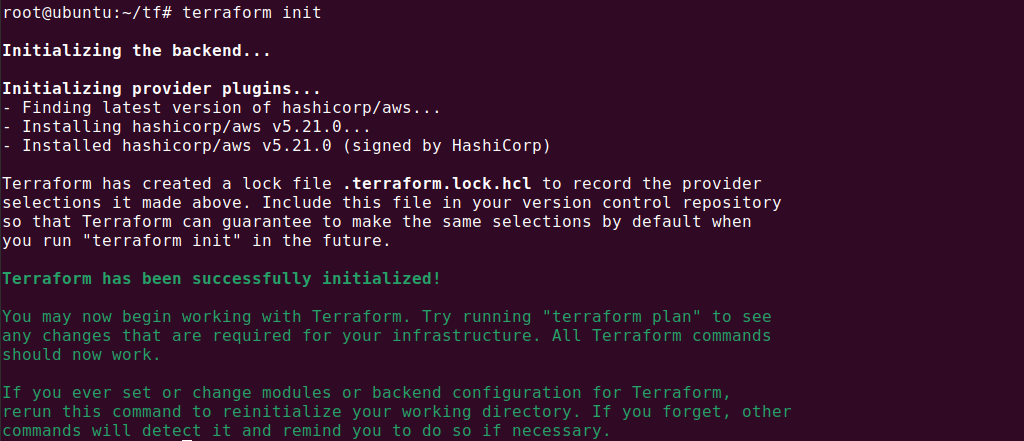
This configuration creates a new AWS instance in the us-west-2 region, using a t2.micro instance type and the specified Amazon Machine Image (AMI).
Step 4: Plan and Apply Configuration
With your configuration written, the next step is to plan and apply it. The terraform plan command is used to create an execution plan. This plan shows what Terraform will do when you call terraform apply. It’s a great way to check your work before making any changes to your infrastructure.
The output of terraform plan should look something like this:
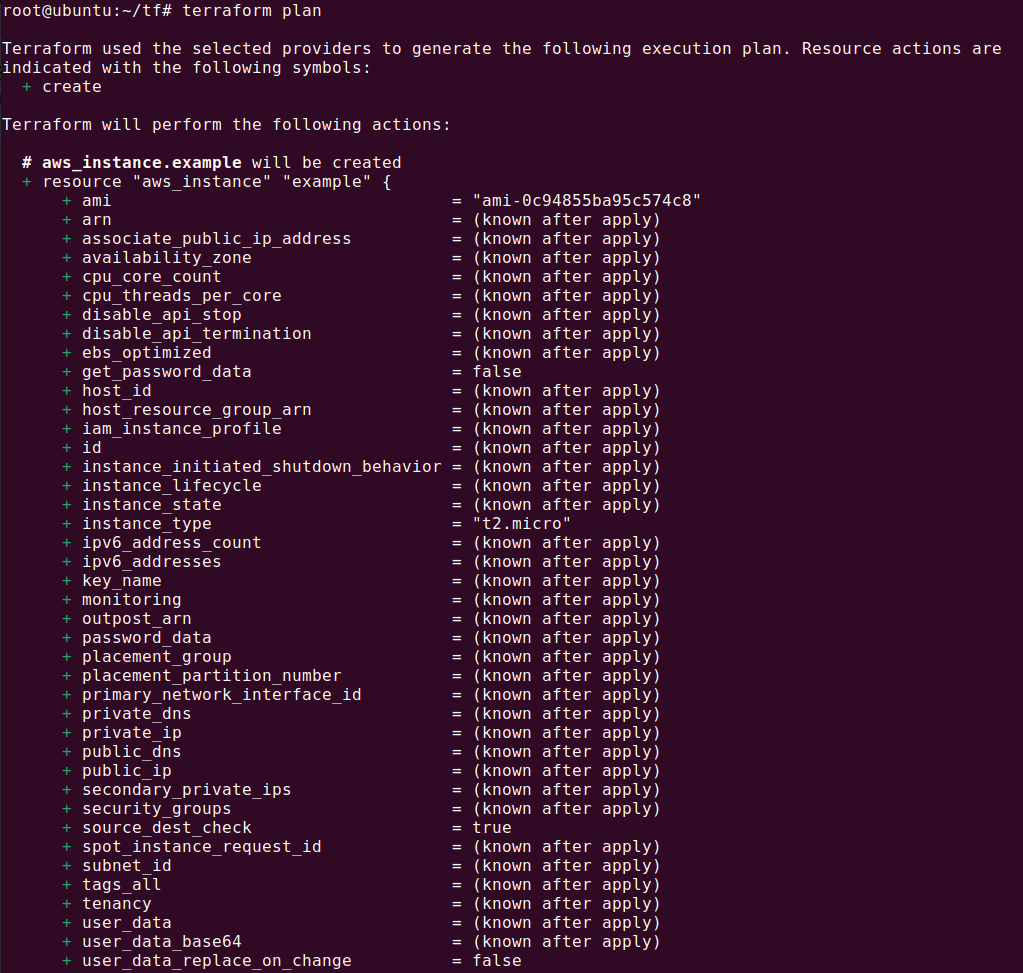
Once you’re satisfied with your plan, you can apply your configuration using the terraform apply command. This command creates, updates, or deletes your resources as defined in your configuration. The output will look something like this:
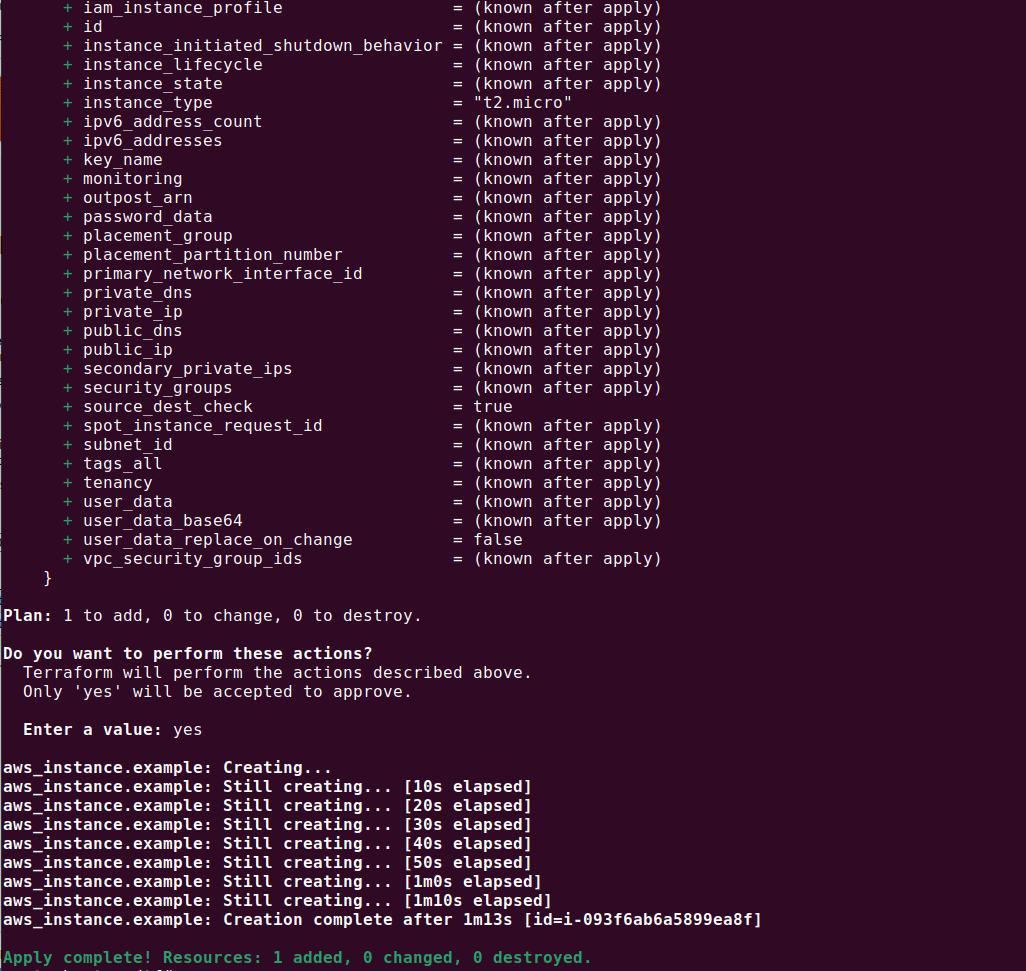
Note: When working in production, the proper workflow is to save the plan and apply it later. But for demo purposes, we are running these two commands on their own.
Related content: Read our guide to infrastructure as code AWS
Infrastructure as Code with Codefresh CI/CD
Codefresh is built for modern tools with support for flexible frameworks. Most infrastructure as code tools are available as docker images and can be seamlessly integrated into Codefresh pipelines – this happens to be a very common pattern for many of our customers. Learn more about how you can easily execute a custom freestyle step with any of these images here.
If you are interested in managing Codefresh resources with Terraform, we also have you covered there! The Codefresh Terraform provider can manage the creation, updates, and removal of Codefresh resources allowing you to utilize your current infrastructure as code workflows without compromises.