Security testing tools help us to monitor our cloud-native resources for potential vulnerabilities throughout our development lifecycle. By flagging security vulnerabilities early, our teams can react on time to reduce potential damage to our end-users and our business.
This post will compare three different Security scanning tools that focus on cloud-native infrastructure and application security, namely:
The goal of any security analysis tool is to enable developers to test code and resources before those are being deployed. Note that for this comparison, we have chosen three enterprise platforms. There are several open-source tools, such as Falco or Clair, that can be used alternatively for certain use cases, which we will reserve for another comparison.
Each tool will be compared based on the following criteria:
| Category | Overview | Quick Highlight |
| CLI vs UI | Is it necessary to use one or the other? Can both tools be combined? |
Snyk is the only tool that offers to scan the dependencies of your application before those are packaged up into container images through the CLI. |
| Pricing | What pricing options are available? | Both Snyk and Aqua follow a similar pricing model which includes a free version with high costs for the enterprise options. Sysdig provides the most flexible pricing option. |
| Available products |
Where does the tool do exceptionally well & in what situations would we want to use it? |
Snyk has the widest product offering, providing both security scanning per programming language, but also a large cloud-native scanning and monitoring product offering. |
| Automation | How far can we automate the integration, scanning, and monitoring? |
Both Snyk and Aqua provide automatic email notifications without requiring any additional set-up. |
| Documentation | How well is the documentation written? | The main difference between each tool was the onboarding and focus of the documentation; Sysdig had the most comprehensive documentation. |
| Integration and UX |
How easy is it to get started and to get results? | All tools had a similar UX and were easy to navigate. The highest level of customization was provided by Sysdig. |
Snyk
Overview
Snyk provides a set of products that are used to enable the secure development of cloud-native applications. The goal is to detect any vulnerabilities during the development process, and before the application is being deployed. Furthermore, Snyk provides continuous scanning of integrated resources and automatically notifies users should it detect any vulnerabilities.
Separately, Snyk has raised a total of $470 million as of the time of writing.
Available Products
Snyk provides a range of products that can be used individually or in combination.
- Snyk Open Source: Scan and manage your open-source repositories; this also includes the Snyk License Compliance.
- Snyk Code: Find and fix vulnerabilities in your application code in real-time during the development process.
- Snyk Container: Find and fix vulnerabilities in container images and Kubernetes applications. Get started with Snyk Container.
- Snyk Infrastructure as Code (IaC): Find and fix insecure configurations in Terraform and Kubernetes code. Get started with Snyk IaC.
- Snyk Intel Vulnerability Database: Comprehensive and actionable open source and container vulnerability data.
Benefits of Snyk Open Source:
- Integrated IDE checks: Snyk provides two IDE integrations, namely Eclipse and JetBrains.
- Native Git Scanning allows you to scan pull requests before they are merged.
- Add an automated Snyk test to your CI/CD pipeline to scan your codebase for vulnerabilities with every deployment.
- Integrated Snyk into your production environment to monitor your codebase for new vulnerabilities and ensure that no new ones are deployed.
- The Reporting Option generates an overview of the discovered vulnerabilities.
- Comprehensive alerts and notification settings with reports right to your inbox weekly.
For this comparison, we focused on Snyk Open Source and Snyk Container.
Pricing
First off, Snyk provides a comprehensive list of features for its free tier, including unlimited tests on open-source projects and up to 200 tests for open source vulnerabilities of private repositories per month. Additionally, you can make use of several integrations.
From there, the pricing is quite steep at $417 per month for up to 10 developers. This option includes unlimited tests, reports, licence compliant management, and access to a rich API. With the last pricing option, you will get additional integrations, such as with Jira, Service Accounts, and advanced project management.
Overall, Snyk is a pretty good deal for open source projects and larger teams as well as teams that can make use of Snyk’s comprehensive feature set.
Integration
Once you sign-up to Snyk, you can integrate with specific git repositories. Snyk will then scan your repositories for vulnerabilities and visualize their findings within the dashboard.
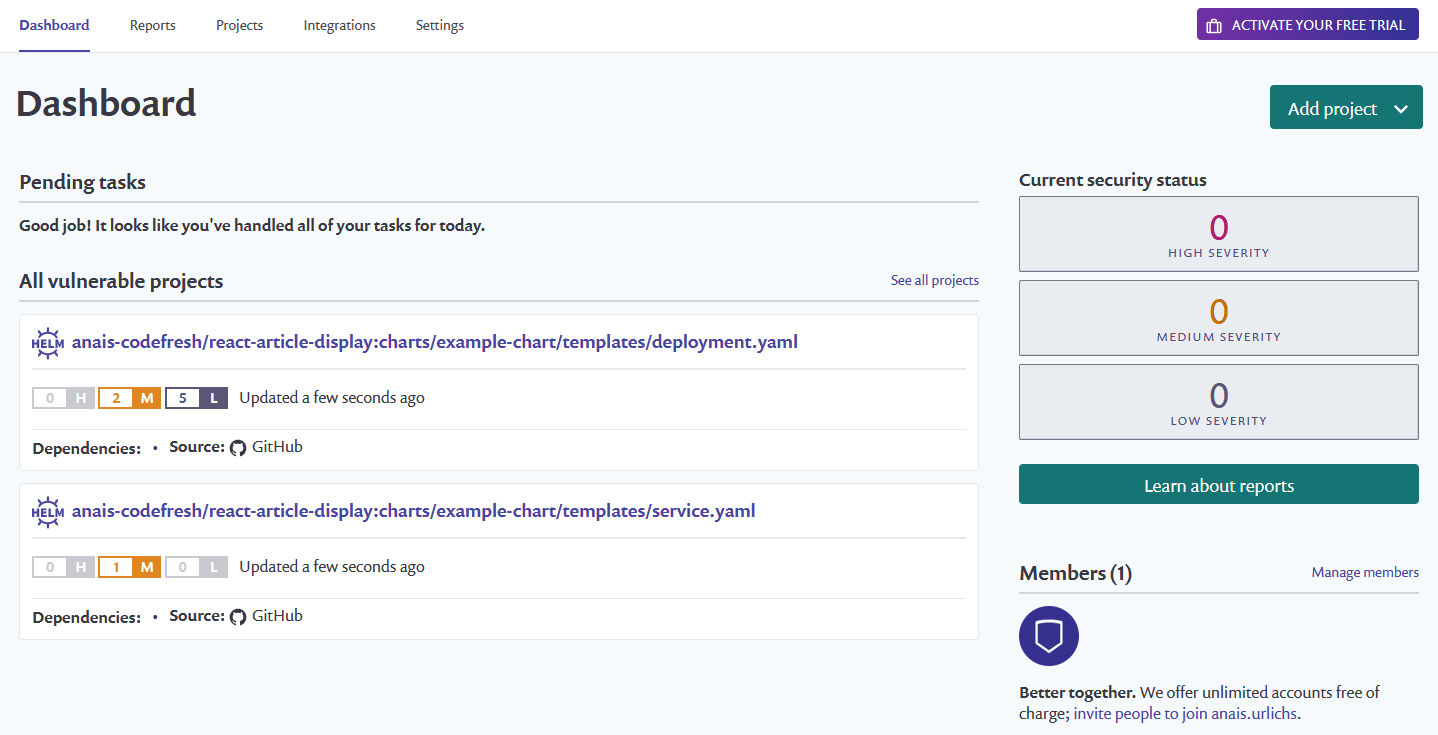
Snyk will build a dependency tree of your project to identify vulnerabilities. In the case of Node.js projects, the information is primarily taken from the package-lock.json file. However, in case Snyk cannot find this file, it will analyze the node_modules folder. To better understand the way vulnerabilities are discovered within Snyk, have a look at the dependency tree of your project.
Automation
Snyk allows users to create a Pull Request to fix security vulnerabilities right through the UI. This feature is available for Java, Ruby, and JavaScript projects.
Furthermore, you can set up notifications to receive reports right to your inbox weekly. By utilizing the Snyk integration settings, users can further automate the scan and reporting process on potential vulnerability issues. Below is a list of integrations that are available to the free account:
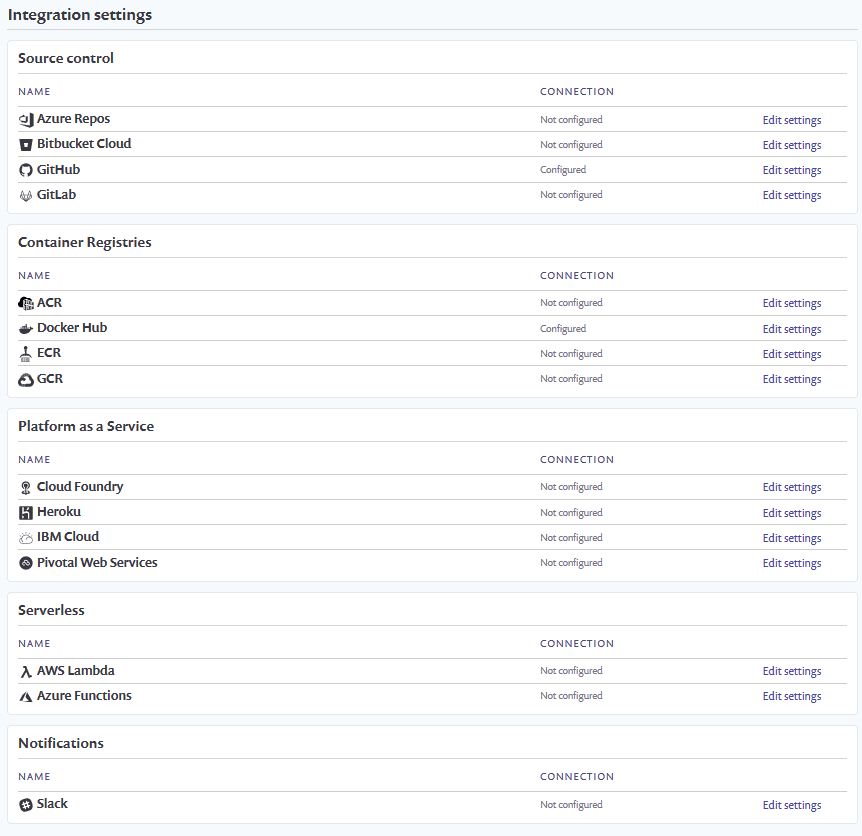
Additionally, Snyk offers CI/CD support. This allows you to integrate Snyk directly with your Codefresh pipeline through a freestyle step as part of your tests.
Documentation
Independent of the complexity of the tool, the documentation is important to help new users to get onboarded and start with your tools as quickly as possible. Overall, the learning curve for Snyk is quite gradual. It takes some time to understand the scope and use case of different products to decide which ones are important for your application. Once you have gained a general understanding of the platform, using their Open Source and Container scanning functionality is a breeze.
CLI vs. UI support
Overall, the Snyk Dashboard is quite intuitive to navigate, the labels are self-explanatory and the important information is color-highlighted.
Separately, Snyk offers a CLI tool that you can install either through npm, brew on Linux and Mac, or scoop on Windows. Once logged into your account, on the Dashboard tap, simply navigate to Add project and select CLI. This will provide you with detailed instructions on how to get started. Additionally, Snyk provides comprehensive documentation for all their tooling.
Aqua
Overview
While Snyk has a high focus on providing security scanning throughout the entire development lifecycle, Aqua’s offering focuses specifically on infrastructure security scanning by integrating with popular cloud providers. This section will take a detailed look at Aqua.
Separately, Aqua just raised a total of $265 million as of the time of writing.
Available Products
Aqua’s Vulnerability Scanning includes the following
- Vulnerability Intelligence Feed: A dashboard on discovered vulnerabilities from across your codebase and analytics insights on the security of your application
- Rich CI/CD integration: Allows users to scan the code based during development
- Scanning Registries and Stored Functions: Discover dependency vulnerabilities early, before deploying containers
- Vulnerability Management Workflow: Provides strategies for managing vulnerabilities and integrating vulnerability discovery into your workflow
- Identifying Vulnerabilities by Image Layer: Check for vulnerabilities in image components before using those across your container images
This is provided through the following products
- Security products for several Cloud Providers: Aqua offers solutions to monitor and secure cloud-native workloads on AWS, Google Cloud, Red Hat, and Azure
- Kubernetes Security is focused on workloads and security of your Kubernetes infrastructure to identify risks within your cluster early
- Docker Security for both the Docker Enterprise and the Docker Community edition
Overall, Aqua provides with each of its product offerings several sub-categories that you can utilize. For instance, as part of the Docker Security offering, you can make use of their secret management.
Pricing
Aqua provides a similar pricing model to Snyk. The free account is for developers, who want to keep track of the security of their infrastructure. Specifically, you can connect to one account, and receive monthly Scan and Compliance reports. Unlike with Snyk, the container security features are only part of the paid plans. The first plan starts at $849 for up to 25 developers. From there, the pricing will scale with the number of developers using the platform. The custom plan provides additional features such as Event Monitoring and Remediation.
Integration/Automation
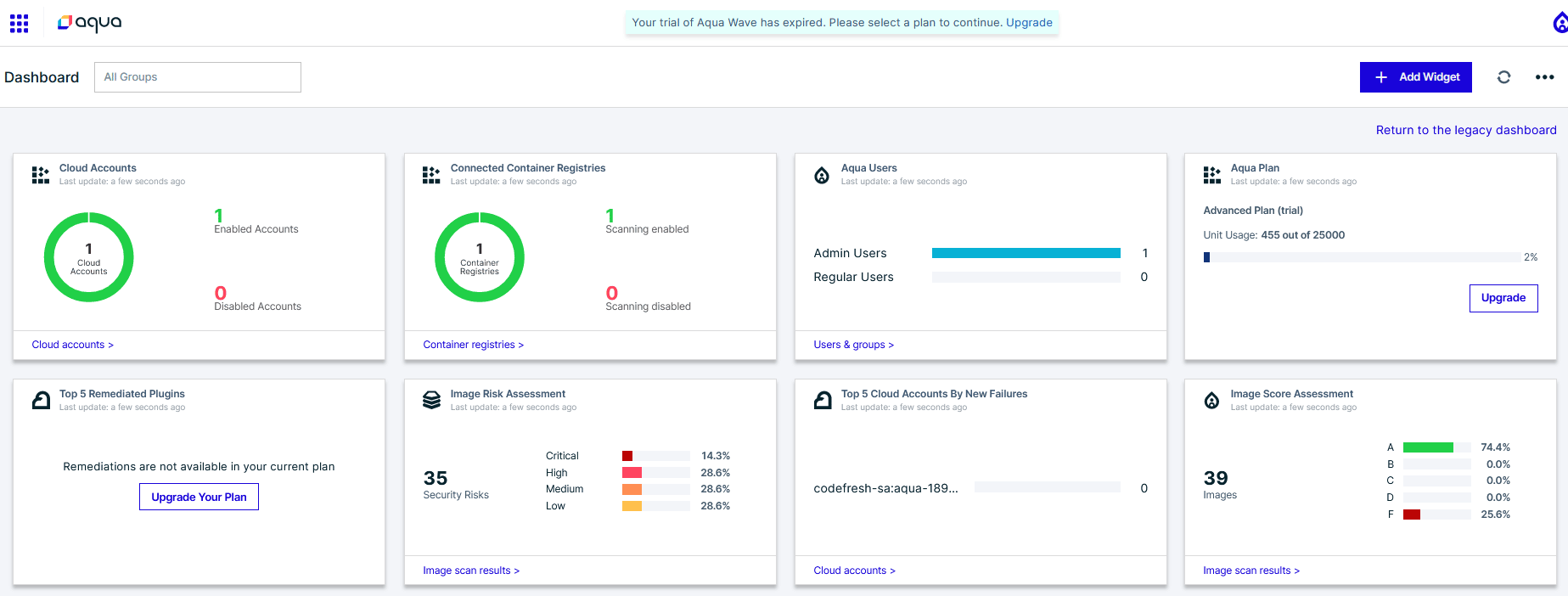
The Dashboard provides an overview of the current vulnerabilities found across the connected infrastructure as well as the container registry. It is extremely modular and allows users to adapt the graphics depending on the data they want to highlight through simply dragging and dropping different components.
Codefresh offers custom integration with Aqua through a custom step that you can use within any Codefresh pipeline. You can find the details on using Aqua in your pipeline in the following blog post. Running the custom step will automatically check your container image for vulnerabilities with every deployment.
Documentation
Once you access your Aqua account, you will be able to view all features but depending on your plan, you will not be able to access everything. If you are on the free tier, all unavailable products will be locked. This allows users to get an idea of the tools that would be available without having to spend much effort going through the offering on the website. However, it might overwhelm users, who only want to make use of a subset of the available features. The screenshot below provides an example of Aqua hiding specific features that require a paid tier.
You can find explanations on each feature on their website, however, there is no direct link to user guides in documentation style format, which would come in handy for smaller teams and free accounts, which do not have access to a personal customer support agent. The only guide that we were able to locate is the enterprise guide, available for paid accounts.
CLI vs. UI support
Aqua focuses on the infrastructure and tools used to run your cloud-native deployments. As such you can integrate Aqua with your existing tools and platforms, initiate scans and view reports through the UI. However, Aqua does not provide a separate CLI that you can access locally through your terminal. As a result, the interface has to be used for all interactions between your infrastructure and Aqua.
Sysdig
Overview
Sysdig provides a range of products to enhance the security of your container and cloud-native solutions. The main differentiator of Sysdig is that it is built on several cloud-native, open-source tools, namely
- Falco: Cloud-native runtime security project
- Prometheus: Open source cluster monitoring tool
While Prometheus is a graduating project of the CNCF foundation, Falco is currently a CNCF incubating project.
Available Products
Sysdig is mainly focused on image scanning and monitoring of your containers and Kubernetes cluster. With this in mind, it provides solutions around the following:
- Image Scanning
- Continuous Compliance
- Runtime Security
- Prometheus Monitoring
- Incident Response & Troubleshooting
Pricing
Sysdig provides comprehensive details around its pricing options. Their pricing page shows a comprehensive comparison of the features provided by each tier. However, they do not provide a free option. Additionally, users will be charged per tool separately, as well as by the number of accounts needed. The ‘Monitoring Essentials’ start at $20, ‘Secure Essentials’ at $40, and the ‘Platform Essentials’ at $50 per month and per user. Below is a brief overview of the features that each part of the platform offers. Please refer to their pricing page for further information.
Platform Essentials
The Platform Essentials provide a comprehensive list of features from across their offerings. This includes comprehensive Dashboards, image scanning, resource monitoring, compliance tracking, and more.
Secure Essentials
The Secure Essentials focus on resource scanning and reporting with fewer features than the Platform Essentials.
Monitor Essentials
Monitor Essentials helps to monitor your resources and visualize their performance in dashboards.
Note that this pricing is billed annually and costs more if paid monthly.
Integration
Once you sign-up to the platform, you will be provided with a set of onboarding steps. For Sysdig to be able to monitor your cluster, you have to install a Helm chart to access the required Kubernetes resources.
The Sysdig UI has two main sections, one for monitoring and one for security that each has a separate onboarding guide. Furthermore, the UI allows users to either utilize Dashboard templates or create their dashboard view:
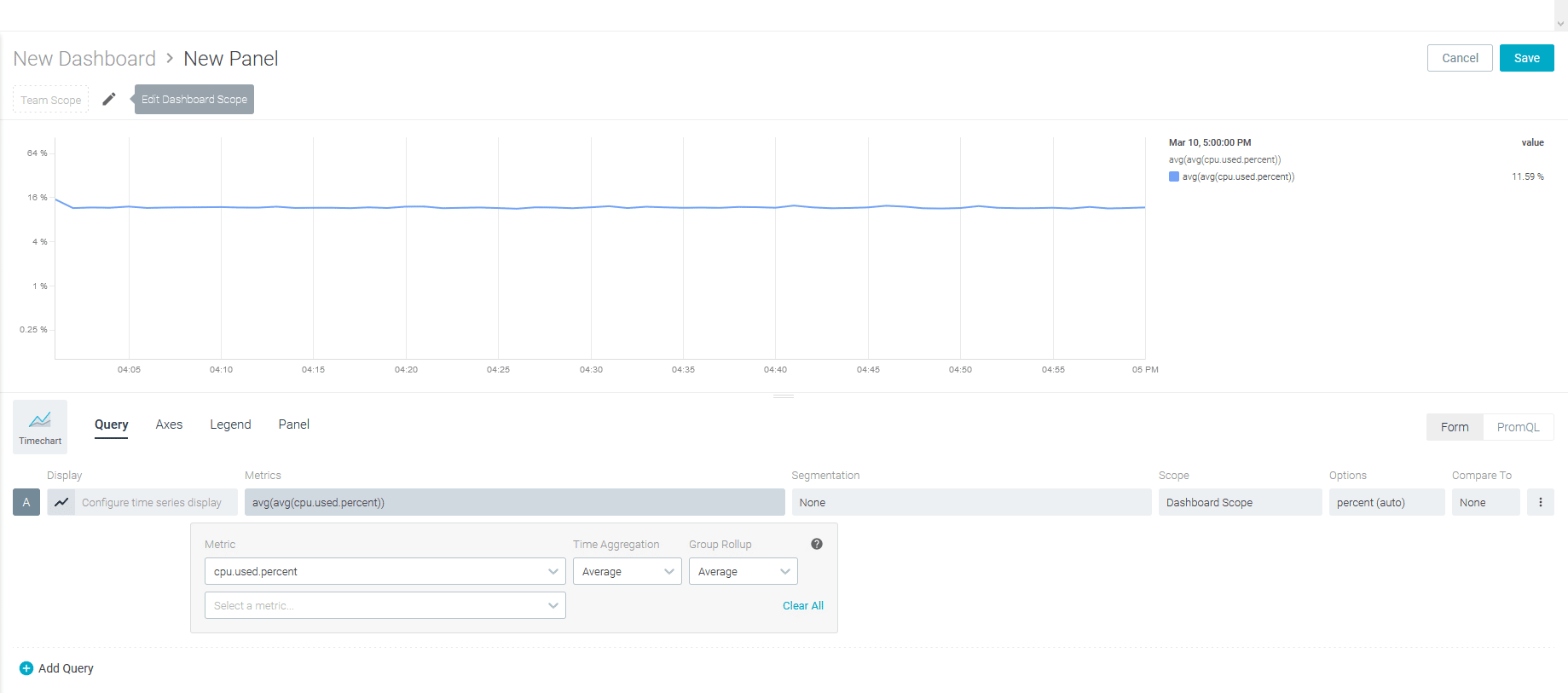
Some additional options include:
- Comprehensive Dashboard showing your cluster resources and the health of those;
- Workloads of the resources deployed on your cluster;
- Compliance monitoring;
- Activity audits;
- And more!
Automation
Sysdig provides a selective list of additional integrations per each product segment. Depending on the tools that you are using, you can add additional integrations to extend the functionality of the platform. For instance, as part of their monitoring solution, you can integrate with Prometheus to collect additional metrics for your application.
Documentation
Sysdig has by far the most comprehensive documentation. It takes a while to navigate since it is divided by product, instead of tools or goal-based. However, once you find the pages of the documentation that correspond to the UI and your use case, it is much easier to use Sysdig to its fullest potential. Sysdig has put a lot of effort into detailing the use of the platform.
Separately, it is worth noting that some integrations might be possible but are not explicitly detailed on their documentation.
CLI vs. UI support
Both the interactions with the CLI as well as the UI have been extremely intuitive and straightforward. While Sysdig requires a few more hoops to install the necessary resources on your cluster, the documentation and UI provide easy onboarding to get everything set up.
Comparison
Both Snyk and Aqua target a similar group of users but for different use cases. Snyk is focused on security scanning during the application development, as well as the scanning of cloud native resources such as your container registry. In comparison, Aqua provides specific products for Cloud security, such as an offering around Infrastructure as Code with Terraform.
Sysdig provides a similar offering but rather than accessing metrics through custom integrations, it utilizes a set of open source tools to display metrics. While it provides detailed insights into your existing resources and comprehensive monitoring of those, it does not provide the same level of container vulnerability scanning as Snyk.
Overall, Snyk and Aqua provide more custom offerings for enterprise clients while Sysdig allows users to combine the different tools available based on their needs. With this in mind, Sysdig is highly flexible in the ways that the platform can be utilized.
If you are a small business with budget constraints or an open-source project, you might want to have a look at the free offering by Snyk or evaluate the pricing by Sysdig. If its features fulfil your requirements, go with Snyk. In comparison, if you are looking for more advanced tooling and support, take a look at ways that Sysdig can be tailored to your needs. In comparison, Aqua does not provide a similar number of features within the free tier.
Deciding between Aqua and Snyk becomes more relevant to large-scale enterprises that require comprehensive tooling and support for those. Additionally, you should take into account the level of support that your team might require to integrate with either platform. In this case, the amount and quality of the documentation become an important factor.
Lastly, all three tools are SaaS-first platforms. However, if you prefer to run the platform on your infrastructure, Sysdig offers an on-prem version while Snyk provides OnPrem services.
| Feature | Snyk | Aqua | Sysdig |
| Free for open source | Yes (limited features) | Yes (limited features) | No, but utilizes open-source tooling |
| Pricing method | Monthly, per user | Monthly, per user | Monthly, per user |
| Pricing starts at | $417 | $849 | $20 |
| Scans libraries | Yes | No | No |
| Scans containers | Yes | Yes | Yes |
| Scans infrastructure | Yes | Yes | Yes |
| Special support for Kubernetes and containers and cloud |
Yes | Yes | Yes |
| Comprehensive API | Yes | N/A | Yes |
| Comprehensive CLI | Yes | No | Yes |
| Easy integrations with other tools |
Yes | Yes | Yes |
| Easy integration with CI/CD | Yes | Yes | Yes |
| Comprehensive documentation | Yes | No | Yes |
| Unique feature | PR with vulnerability fixes & CLI tool |
VM and Serverless Security |
Design your Dashboard |
| Great for whom? | Open source and enterprises | Large enterprises | Smaller companies |
Summary
This article provided a comprehensive overview of three of the major security scanning tools available within the cloud-native ecosystem. The focus was placed on the onboarding experience, their product offerings, and integration with other tools. Additionally, the pricing and different ways to customize the platform were taken into account to make recommendations.
