Secret management is one of the most critical areas in deploying and running applications. Codefresh already had native support for native Kubernetes secrets or custom secrets on the Codefresh Runner, but more and more customers have asked us for native support for Hashicorp Vault.
Today we are pleased to announce our native integration with Hashicorp vault as another secret provider for Codefresh pipelines. The existing Vault pipeline plugin can still be used, but the new native integration makes the process much more intuitive and secure.
Connecting your Hashicorp vault instance
To begin the integration you need an instance of Hashicorp vault. The location of the Vault can be either or the public cloud or within your premises behind the firewall.
Next, you need to choose the method that Codefresh will authenticate to vault. The following methods are supported:
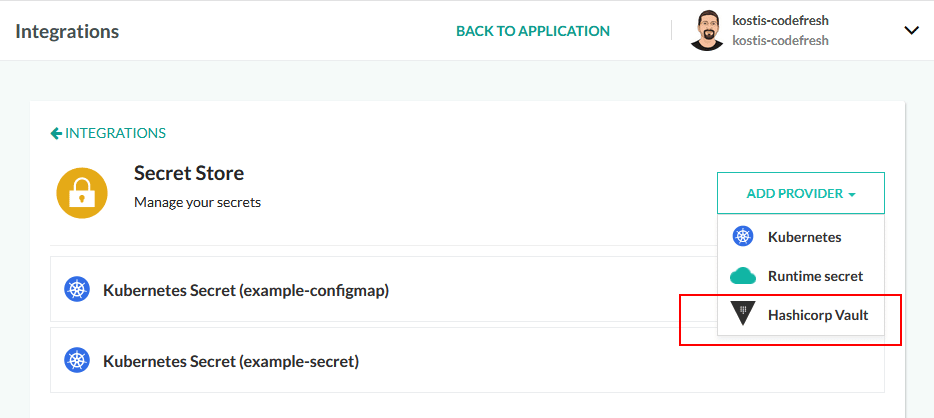
Next, go to your secret integration settings in your Codefresh account and select Vault from the drop-down menu.
On the configuration screen, you can give Codefresh the credentials it needs to access your Hashicorp Vault instance. Unlike our Vault plugin, you can now take advantage of more authentication methods in addition to token and app/role
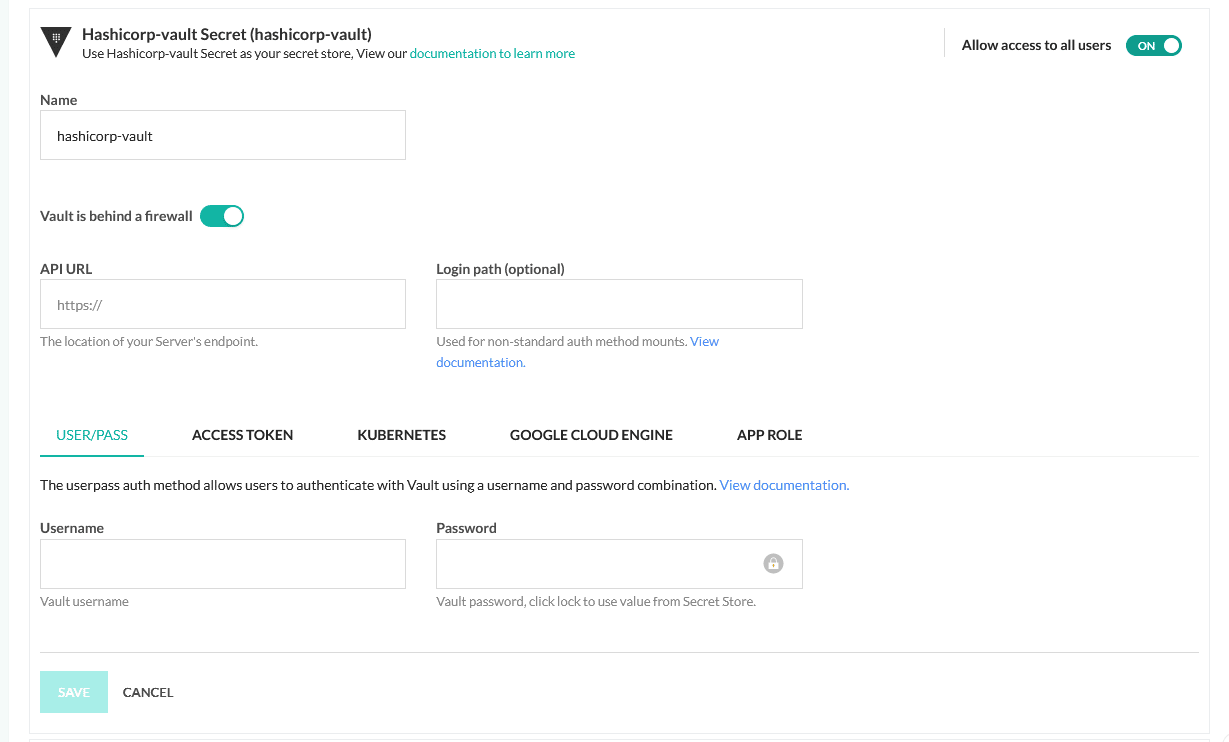
.
Following the same procedure, you can add more connections to other Vault instances that you have. Remember to note down the name that you use for each integration as you will need it inside your pipeline later to distinguish between different Vault installations (if you use more than one with Codefresh).
Using Hashicorp Vault secrets in your pipelines
With the initial setup out of the way, you can now use Vault secret like any other secret in any pipeline as well as the Codefresh UI.
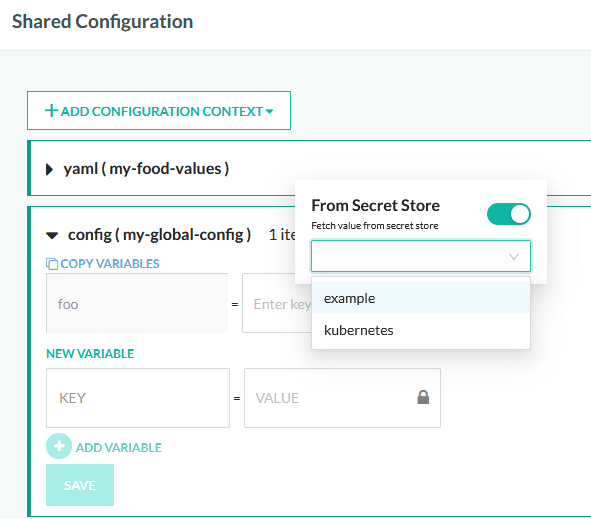
For the GUI, simply click on the small lock icon in a supported field and select your secret.
Using Hashicorp Vault secrets in your pipelines
With the initial setup out of the way, you can now use Vault secret like any other secret in any pipeline as well as the Codefresh UI.
For the GUI, simply click on the small lock icon in a supported field and select your secret.
For a pipeline just mention the secret with the familiar secret syntax:
version: '1.0'
steps:
step:
type: freestyle
arguments:
image: alpine
environment:
- SECRET=${{secrets.my-vault-store-name.path/to/secret@my-key}}
commands:
- echo $SECRET
It is that easy! Remember that you can mix and match secrets from different sources (and even different vault installations) in the same pipeline. But the way you access secrets is unified regardless of the actual secret storage.
For more details see our Vault documentation.
New to Codefresh? Create Your Free Account today!