Ingress configuration for GitOps Runtimes
Configure ingress controllers for GitOps Runtimes
Ingress controller configuration
Codefresh supports both tunnel-based and ingress-based access modes when installing GitOps Runtimes.
Ingress-based access mode requires you to configure an ingress controller before the installation, and pass additional flags such as the ingress host and class in the Helm install command.
See also GitOps Runtime architecture.
Ambassador ingress configuration
For detailed configuration information, see the Ambassador ingress controller documentation.
This section lists the specific configuration requirements for Codefresh to be completed before installing the Hybrid GitOps Runtime.
- Valid external IP address
- Valid TLS certificate
- TCP support
Valid external IP address
Run kubectl get svc -A to get a list of services and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure installation, the ingress controller must have a valid TLS certificate.
TIP
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
AWS ALB ingress configuration
For detailed configuration information, see the ALB AWS ingress controller documentation.
This table lists the specific configuration requirements for Codefresh.
| What to configure | When to configure |
|---|---|
| Valid external IP address | Before installing Hybrid GitOps Runtime |
| Valid TLS certificate | |
| TCP support | |
| Controller configuration] | |
| Alias DNS record in route53 to load balancer | After installing Hybrid GitOps Runtime |
| (Optional) Git integration registration |
Valid external IP address
Run kubectl get svc -A to get a list of services and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure runtime installation, the ingress controller must have a valid TLS certificate.
TIP:
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
Controller configuration
In the ingress resource file, verify that spec.controller is configured as ingress.k8s.aws/alb.
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
name: alb
spec:
controller: ingress.k8s.aws/alb
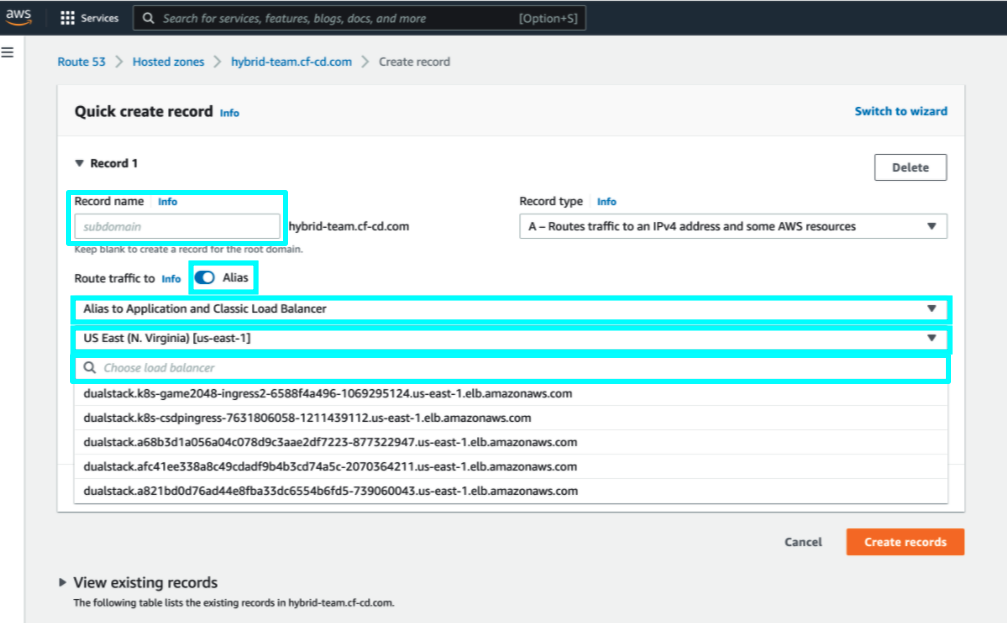
Create an alias to load balancer in route53
IMPORTANT
Configure the alias after installing the Hybrid GitOps Runtime.
- Make sure a DNS record is available in the correct hosted zone.
- After Hybrid GitOps Runtime installation, in Amazon Route 53, create an alias to route traffic to the load balancer that is automatically created during the installation:
- Record name: Enter the same record name used in the installation.
- Toggle Alias to ON.
- From the Route traffic to list, select Alias to Application and Classic Load Balancer.
- From the list of Regions, select the region. For example, US East.
- From the list of load balancers, select the load balancer that was created during installation.
For more information, see Creating records by using the Amazon Route 53 console.
(Optional) Git integration registration
If the installation failed, as can happen if the DNS record was not created within the timeframe, manually create and register Git integrations using these commands:
cf integration git add default --runtime <RUNTIME-NAME> --api-url <API-URL>
cf integration git register default --runtime <RUNTIME-NAME> --token <RUNTIME-AUTHENTICATION-TOKEN>
Istio ingress configuration
For detailed configuration information, see Istio ingress controller documentation.
The table below lists the specific configuration requirements for Codefresh.
| What to configure | When to configure |
|---|---|
| Valid external IP address | Before installing Hybrid GitOps Runtime |
| Valid TLS certificate | |
| TCP support | |
| Cluster routing service | After installing Hybrid GitOps Runtime |
Valid external IP address
Run kubectl get svc -A to get a list of services and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure runtime installation, the ingress controller must have a valid TLS certificate.
TIP
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
Cluster routing service
IMPORTANT
Configure the cluster routing service after installing the Hybrid GitOps Runtime.
Based on the Hybrid GitOps Runtime version, you need to configure single or multiple VirtualService resources for the app-proxy, webhook, and workflow services.
Runtime version 0.0.543 or higher
Configure a single VirtualService resource to route traffic to the app-proxy, webhook, and workflow services, as in the example below.
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
namespace: pov-codefresh-istio-runtime # replace with your Hybrid GitOps runtime name
name: internal-router
spec:
hosts:
- pov-codefresh-istio-runtime.sales-dev.codefresh.io # replace with your host name
gateways:
- istio-system/internal-router # replace with your gateway name
http:
- match:
- uri:
prefix: /webhooks
route:
- destination:
host: internal-router
port:
number: 80
- match:
- uri:
prefix: /app-proxy
route:
- destination:
host: internal-router
port:
number: 80
- match:
- uri:
prefix: /workflows
route:
- destination:
host: internal-router
port:
number: 80
Runtime version 0.0.542 or lower
Configure two different VirtualService resources, one to route traffic to the app-proxy, and the second to route traffic to the webhook services, as in the examples below.
VirtualService example for app-proxy:
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
namespace: test-runtime3 # replace with your Hybrid GitOps runtime name
name: cap-app-proxy
spec:
hosts:
- my.support.cf-cd.com # replace with your host name
gateways:
- my-gateway # replace with your host name
http:
- match:
- uri:
prefix: /app-proxy
route:
- destination:
host: cap-app-proxy
port:
number: 3017
VirtualService example for webhook:
Configure a
uri.prefixanddestination.hostfor each event-source if you have more than one.
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
namespace: test-runtime3 # replace with your Hybrid GitOps runtime name
name: csdp-default-git-source
spec:
hosts:
- my.support.cf-cd.com # replace with your host name
gateways:
- my-gateway # replace with your gateway name
http:
- match:
- uri:
prefix: /webhooks/test-runtime3/push-github # replace `test-runtime3` with your Hybrid GitOps runtime name, and `push-github` with the name of your event source
route:
- destination:
host: push-github-eventsource-svc # replace `push-github' with the name of your event source
port:
number: 80
- match:
- uri:
prefix: /webhooks/test-runtime3/cypress-docker-images-push # replace `test-runtime3` with your Hybrid GitOps runtime name, and `cypress-docker-images-push` with the name of your event source
route:
- destination:
host: cypress-docker-images-push-eventsource-svc # replace `cypress-docker-images-push` with the name of your event source
port:
number: 80
NGINX Enterprise ingress configuration
For detailed configuration information, see NGINX ingress controller documentation.
The table below lists the specific configuration requirements for Codefresh.
| What to configure | When to configure |
|---|---|
| Verify valid external IP address | Before installing Hybrid GitOps Runtime |
| Valid TLS certificate | |
| TCP support | |
| NGINX Ingress: Enable report status to cluster | |
| NGINX Ingress Operator: Enable report status to cluster | |
| Patch certificate secret | After installing Hybrid GitOps Runtime |
Valid external IP address
Run kubectl get svc -A to get a list of services and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure runtime installation, the ingress controller must have a valid TLS certificate.
TIP
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
NGINX Ingress: Enable report status to cluster
If the ingress controller is not configured to report its status to the cluster, Argo’s health check reports the health status as “progressing” resulting in a timeout error during installation.
- Pass
--report-ingress-statustodeployment.
spec:
containers:
- args:
- --report-ingress-status
NGINX Ingress Operator: Enable report status to cluster
If the ingress controller is not configured to report its status to the cluster, Argo’s health check reports the health status as “progressing” resulting in a timeout error during installation.
-
Add this to the
Nginxingresscontrollersresource file:... spec: reportIngressStatus: enable: true ... -
Make sure you have a certificate secret in the same namespace as the Hybrid GitOps Runtime. Copy an existing secret if you don’t have one. You will need to add this to the
ingress-masterwhen you have completed runtime installation.
Patch certificate secret
IMPORTANT
The certificate secret must be configured after installing the Hybrid GitOps Runtime.
Patch the certificate secret in spec.tls of the ingress-master resource.
The secret must be in the same namespace as the Hybrid GitOps Runtime.
- Go to the Hybrid GitOps Runtime namespace with the NGINX ingress controller.
-
In
ingress-master, add tospec.tls:tls: - hosts: - <host_name> secretName: <secret_name>
NGINX Community version ingress configuration
Codefresh has been tested with and supports implementations of the major providers. For your convenience, we have provided configuration instructions, both for supported and untested providers in Provider-specific configuration.
This section lists the specific configuration requirements for Codefresh to be completed before installing the Hybrid GitOps Runtime.
- Verify valid external IP address
- Valid TLS certificate
- TCP support
Valid external IP address
Run kubectl get svc -A to get a list of services, and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure runtime installation, the ingress controller must have a valid TLS certificate.
TIP
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
Here’s an example of TCP configuration for NGINX Community on AWS.
Verify that the ingress-nginx-controller service manifest has either of the following annotations:
service.beta.kubernetes.io/aws-load-balancer-backend-protocol: "tcp"
OR
service.beta.kubernetes.io/aws-load-balancer-type: nlb
Provider-specific configuration
NOTE
The instructions are valid fork8s.io/ingress-nginx, the community version of NGINX.
AWS
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/aws/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Azure (AKS)
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Bare Metal Clusters
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/baremetal/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Digital Ocean
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/do/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Docker Desktop
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Note: By default, Docker Desktop services will provision with localhost as their external address. Triggers in delivery pipelines cannot reach this instance unless they originate from the same machine where Docker Desktop is being used.
Exoscale
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/main/deploy/static/provider/exoscale/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Google (GKE)
Add firewall rules
GKE by default limits outbound requests from nodes. For the Hybrid GitOps Runtime to communicate with the control-plane in Codefresh, add a firewall-specific rule.
- Find your cluster's network:
gcloud container clusters describe [CLUSTER_NAME] --format=get"(network)" - Get the Cluster IPV4 CIDR:
gcloud container clusters describe [CLUSTER_NAME] --format=get"(clusterIpv4Cidr)" - Replace the `[CLUSTER_NAME]`, `[NETWORK]`, and `[CLUSTER_IPV4_CIDR]`, with the relevant values:
gcloud compute firewall-rules create "[CLUSTER_NAME]-to-all-vms-on-network"
--network="[NETWORK]" \
--source-ranges="[CLUSTER_IPV4_CIDR]" \
--allow=tcp,udp,icmp,esp,ah,sctp
Use ingress-nginx
- Create a `cluster-admin` role binding:
kubectl create clusterrolebinding cluster-admin-binding \
--clusterrole cluster-admin \
--user $(gcloud config get-value account)
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
MicroK8s
- Install using Microk8s addon system:
microk8s enable ingress - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
MiniKube
- Install using MiniKube addon system:
minikube addons enable ingress - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Oracle Cloud Infrastructure
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Scaleway
- Apply:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/scw/deploy.yaml - Verify a valid external address exists:
kubectl get svc ingress-nginx-controller -n ingress-nginx
Traefik ingress configuration
For detailed configuration information, see Traefik ingress controller documentation.
The table below lists the specific configuration requirements for Codefresh.
| What to configure | When to configure |
|---|---|
| Valid external IP address | Before installing Hybrid GitOps Runtime |
| Valid SSL certificate | |
| TCP support | |
| Enable report status to cluster |
Valid external IP address
Run kubectl get svc -A to get a list of services and verify that the EXTERNAL-IP column for your ingress controller shows a valid hostname.
Valid TLS certificate
For secure runtime installation, the ingress controller must have a valid TLS certificate.
TIP
Use the FQDN (Fully Qualified Domain Name) of the ingress controller for the TLS certificate.
TCP support
Configure the ingress controller to handle TCP requests.
Enable report status to cluster
By default, the Traefik ingress controller is not configured to report its status to the cluster. If not configured, Argo’s health check reports the health status as “progressing”, resulting in a timeout error during installation.
To enable reporting its status, add publishedService to providers.kubernetesIngress.ingressEndpoint.
The value must be in the format "<namespace>/<service-name>", where:
<service-name> is the Traefik service from which to copy the status
...
providers:
kubernetesIngress:
ingressEndpoint:
publishedService: "<namespace>/<traefik-service>" # Example, "codefresh/traefik-default"
...
Related articles
Runtime prerequisites
Install GitOps Runtime with existing Argo CD
Install GitOps Runtime with new Argo CD